As someone who has been heavily involved in one darknet (Anonet) and helped start another (Underlink, which is now mostly defunct), I will attempt to share my experiences and understanding of them here. Please feel free to edit this answer to provide additional details or to correct anything.
Definition
"Darknet" is a tricky word that has a few different definitions, the most general of which is a private network with internet-like routing between peers. This is a very broad definition; darknets vary greatly in their structure. Some examples of darknets include:
- Anonet and Anonet6, an IPv4 and sister IPv6 darknet with the goal of being completely decentralized and anonymous
- Underlink, an IPv6-only darknet built by former Anonet members, with a focus more on hobbyism rather than complete anonymity, and was more centralized than Anonet.
- Seattle Wireless, a meshnet1 operating in the Seattle area.
- Tor is a not like the sample darknet I will describe below, but falls under the definition of a darknet, as it is comprised of a series of exit nodes that route traffic2.
What a Darknet Provides
As the question notes, it's difficult to remain anonymous on the internet while retaining the ability to communicate with a large number of users. On the internet, every website you communicate with receives your ISP-issued IP, which gives them your approximate location, and can be used with at least some reliability to track your actions.
By contrast, darknets allow you to use an internal, non-globally routed IP address when accessing resources hosted on the darknet. Participants in the darknet, excluding your direct peers, will never be able to see your real IP address, but will still be able to communicate with you using virtually any peer-to-peer application (HTTP, email, BitTorrent, FTP, SSH, ...).
An Example Darknet
I will describe an example darknet. This should be enough detail for you to at least get started in forming your own darknet. You will, however, need to do additional research. There are many approaches to structuring a darknet, and you will want to make informed decisions as you plan yours out. Darknets are a great way to learn more about networking. I highly recommend participating in one to anybody interested in the topic.
Peerings
Darknets, like the internet, are built on the idea of peerings. Anyone interested in joining the network's routing infrastructure needs to peer with one or more existing participants on the network. This forms a redundant web of participants, allowing the network to expand.
In order to peer with somebody, all you really need is a direct connection to them (and their cooperation). You can connect an ethernet cable from their machines (or routers) to yours, or you can setup a virtual ethernet tunnel using VPN software3. The benefit of using virtual tunnels instead of physical infrastructure (ethernet links, wireless connections) is that your network can span the globe easily and cheaply. Using physical links limits you to participants in your physical area, limiting the potential size and adoption of your darknet. The main disadvantage of using virtual tunnels is that you remain dependent on ISPs and governments allowing you to have access to the internet4.
Routing
Assuming that you have managed to connect two machines together, I will now explain the most important component of a functioning darknet: routing. There are several types of routing you can use. Tor, for example, uses onion routing. For the sake of this example setup, though, we'll use a more traditional routing scheme: BGP routing5.
In a BGP routing setup, each participant is an "autonomous system" (AS). Each AS has its own set of IP space to do whatever it wants with. These ASes are identified with a number (an "ASN"), which is unique across the entire network (the internet or the darknet, depending on the context). You can see a list of AS numbers in use on the internet here.
Let's say I want to peer with my friend, chris (I am lex). We each have picked an AS number (I am 3090, chris is 404). In order to peer, we need to do just two things:
- Establish a connection between our routers (often VPSes or generic Linux boxes hosted at some datacenter). We will probably use a virtual tunnel (VPN) to do this.
- Configure our BGP daemons to advertise our peering to the rest of the network, and to establish routing with each other6.
Each network participant will typically want to have multiple peers to provide redundancy. This is, however, a security risk, because each peer will know your true IP address. As such, you want to peer only with people you trust (not just trust as a person, but also trust to keep their machine secure from hackers or the authorities to protect your identity).
A sample network map will look like this (this is an old visual map of the actual BGP setup on Anonet6):
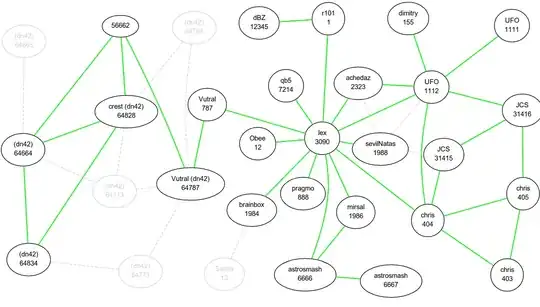
Each bubble represents a participant doing routing on Anonet. Typically each machine here would get a /24 (the above map is of ano6, but I'll use IPv4 terminology because it's easier to grasp for more people), and be free to assign addresses inside that however it wanted; that machine would handle final routing for them.
So let's say that I am AS3090 (lex, in the middle). AS3090 is actually a dedicated machine in some datacenter. For convenience, all of my personal computers connect to my server using some standard VPN software (OpenVPN, in this case), and are given addresses on AS3090's /24. This way, my laptops/tablets/desktops, which don't have static IPs, don't have to worry about peering. They let the dedicated server handle that for them.
If one of my machines connected to AS3090 wants to send a packet to a machine in AS31416 (far right of the map), it has a few simple options:
AS3090 (lex) -> AS1112 (UFO) -> AS31416 (JCS)
AS3090 (lex) -> AS404 (chris) -> AS31415 (JCS) -> AS31416 (JCS)
AS3090 (lex) -> AS404 (chris) -> AS405 (chris) -> AS31416 (JCS)
AS3090 (lex) -> AS2323 (achedaz) -> AS1112 (UFO) -> AS31416 (JCS)
(this is just a subset of possible paths)
This is all part of the BGP routing framework.
The first path in my list is the shortest (in number of hops, not necessarily in terms of latency, since each hop could be, and often is, located on a different continent), so the packets will take that path there. The response packets may well take a different path back, but that's not important; as long as the packets get to the origin, the two machines can still talk. It's not uncommon to see outgoing packets leave on one interface and responses returning on a different interface. Your OS won't care.
The beauty of this setup is that it functions just like the real internet (in fact, core parts of the internet use BGP routing just like this). If AS3090 (lex) loses its connection with AS1112 (UFO), then the packets will automatically choose a different path to AS31416. It's redundant in this way.
Why This Provides Anonymity
This also makes darknets very good for anonymity. If I am AS12345 (dBZ, top middle), the only person on the entire network who knows my true IP is my only peer, AS1 (r101). The rest only see my internal IP inside AS12345's subnet. For authorities, or anybody else, to find out AS12345's location/IP, they have to follow the chain of peers and break each one to find out who they're connecting with. This can be extremely expensive on large darknets, since peers often cross borders (in Anonet, we often planned out to cross borders to make it especially tricky).
Growing Pains
This stuff is pretty easy once you understand it. The hard part in growing a network like this is that it's decentralized. Anonet split in half multiple times during its life. The peering between AS3090 (lex) and AS757 (Vutral) could break at any minute, and those two halves of Anonet would completely cease to be connected. But the people in each half would still be able to talk to eachother. You can cut the darknet in half and it still survives.
Typing in a friend's IP address to access their services (websites, file sharing, whatever) isn't fun. You want DNS, right? Well, that requires some central authority to make sure nobody is infringing on eachothers' claims. On Anonet, the way we "solved" that was with something called "resdb": a git repo containing a set of claims. Anybody could make claims and commit changes. The key was to get others to accept your changes into their copy of the git repo. This meant that different people had different versions of the repo, so for some people a domain doesn't exist, for others it does, and for others it might exist but point somewhere completely different. (resdb contained a set of files and scripts to generate zone files for BIND and similar so that anyone could run their own DNS server for the ano. TLD).
But you don't just need DNS reservations to be unique. IP allocations should be unique, too. Wouldn't we all like to be 172.16.0.0/24? If multiple people are using that, we get conflicts, which means that those go in resdb as well and you need to convince people to accept your claims. You also need to handle AS number reservations and a dozen other things that ICANN handles on the internet. It turns into a big mess and it's very hard to scale since there is no central authority which has the final say on reservations.
I can't stress enough how big of a mess resdb ended up being. Underlink attempted to solve these problems by sacrificing some of the decentralization of Anonet for the sake of convenience. There was a central authority that handled DNS registrations and ASN/IP allocations, and it worked pretty well for Underlink's short life (about a year). Underlink never took off, but I do think its model is preferable in many cases. It all depends on the central authority remaining benign and secure. The whole reason we started a darknet was that we didn't want to live under ICANN's rules. Both approaches clearly have merits.
Conclusion
I hope this gave you a bit of an idea of what a darknet is. Again, this is not a full definition, it's just based on my experiences, and a lot of it isn't really relevant to your goal. I know, for example, that some people have attempted to create darknets by using consumer routers flashed with DD-WRT (to connect geographically close peers together) rather than using the existing infrastructure on the internet.
If you have any questions, please feel free to ask for clarification. I'm no expert, but I have played around with this stuff quite a bit just out of pure interest.
If you have knowledge to add, please go ahead and edit this response. I've made it community wiki to encourage that.
1. A meshnet is usually defined as a darknet that operates over participant-controlled physical links, such as broadcasting wireless routers or physical network cables. By contrast, most darknets use the existing infrastructure of the internet, connecting peers via virtual tunnels (VPNs) instead of physical links. Meshnets are thus much more limited in size, but they do provide additional benefits.
2. This is a pretty big simplification as I'm not entirely familiar with how Tor operates, and the rest of this post is focused more on a traditional darknet that uses internet-like routing rather than onion routing.
3. In the past, I have used QuickTun, SigmaVPN, and OpenVPN. Really, though, any software which allows you to have a virtual ethernet tunnel with a remote machine will work. It doesn't even have to encrypt the connection (but this is a really good idea, and all of the software examples above do provide encryption).
4. While your ISP or government won't easily be able to tell you are participating in a darknet if you use encrypted tunnels (all they will see is an encrypted VPN connection), it will probably look suspicious, and they could certainly prevent you from making the initial VPN connection.
5. BGP routing is used in many darknets, including Anonet and Underlink. Onion routing, and other more exotic routing schemes, do have their merits, but they can make it a lot harder for people to join your network (support for BGP routing is widespread and standardized, since it's what the internet uses). BGP routing is both redundant and can provide decent anonymity, so there's no reason to write it off, but looking at alternatives isn't a bad idea.
6. An example BGP routing configuration for a peering looks something like this:
protocol bgp bgp_chris_underlink_core
{
table underlink_core; # routing table
local as 3090; # my ASN
neighbor 172.16.10.1 as 404; # partner (chris') IP address for the virtual tunnel interface, and his ASN
source address 172.16.9.1; # my IP address virtual interface
# a series of filters to ensure chris can't send me bad routes
import filter underlink_filter_core;
export filter underlink_filter_core;
};
This example uses bird, but other BGP daemons will be configured in a similar way. I have only used bird, but there are many variaties of BGP routing software available. Since it's a standardized protocol, it's not necessary that you and your peering partner use the same BGP software. You could even use an enterprise-grade router with a proprietary BGP client against his $15/m Linux VPS running bird.
