I started reading "Hacking, The Art of Exploitation" and I am confused about some things regarding memory examination.
When I disassemble main, I get an output of all memories where the individual assembly instructions are, right? Each instruction does not necessarily need to append the memory address by one, that is why I might have <main+1> and then <main +3> right after. In the following picture the first 20 instructions for the program are shown. 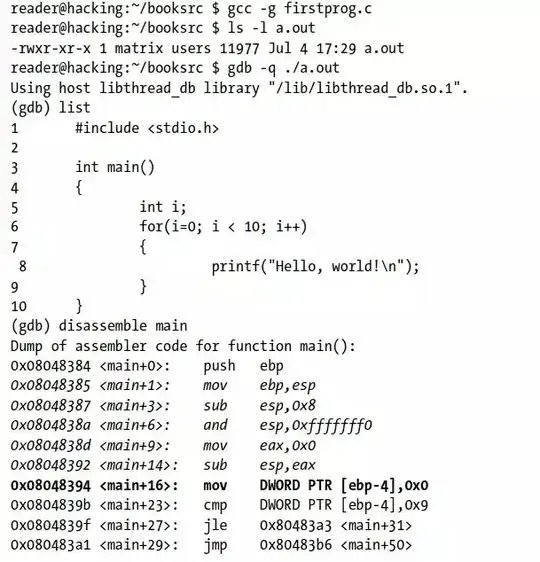 How many bytes of information does each information contain?
How many bytes of information does each information contain?
Now I get confused, when using i r eip, I get the location of this register, which is 0x8048384 (so is it stored as the first instruction of main?) 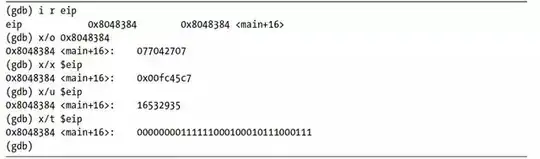 . The value next to it, is the value it holds, here I wonder, it stores
. The value next to it, is the value it holds, here I wonder, it stores 0x00fc45c7, however this instruction is not in the output above? I thought it should point to the memory which consists the next instruction for the program.
Now comes the biggest confusion, I can observe the memory where $eip is stored and observe multiple units at once, which can be seen on here:  However on this screenshot using
However on this screenshot using x/2x
you can see that there are two values stored in the memory and both of 4 bytes in size? Then using x/12
there are suddenly 4 words in 0x8048384 and other 4 words 0x8048394?
I just don't seem to understand how the values stored in the memory address differ based on the units I use. I also thought each memory address should contain only a byte of information?