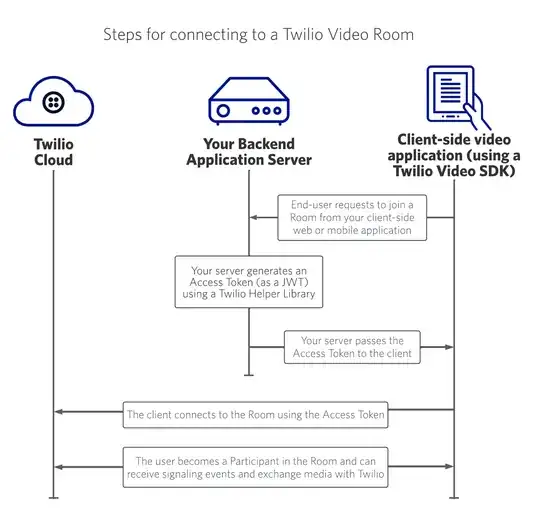
I am currently following the instructions for getting an access token on behalf of a Twilio user described here
The part that is confusing me where it seems to generate an access token then proxy it back to the client. I guess the idea is the access token is being made for the user on behalf of the application but that seems off to me. Is this a correct way to handle geting an access token to the browser? Are there limits to when you can pass back access tokens (besides ssl)? Shouldn't it be using a refresh token?
An example of how this works in practice see this example...
const token = new AccessToken(
process.env.TWILIO_ACCOUNT_SID,
process.env.TWILIO_API_KEY,
process.env.TWILIO_API_SECRET
);
...
app.get('/', function(request, response) {
const identity = request.query.identity || 'identity';
const room = request.query.room;
response.send(tokenGenerator(identity, room));
});
https://github.com/TwilioDevEd/video-access-token-server-node/blob/master/index.js