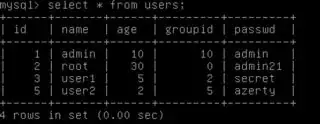
I am trying to understand The Pentester Lab challenge here at VulnHub.
After I translated this tutorial into English, at Exercise 2 I was presented with the following SQLi which completes the challenge:
http://pentesterlab/sqli/example2.php?name=root'/**/union/**/select/**/1,(select/**/name/**/from/**/users/**/limit/**/3,1),(select/**/passwd/**/from/**/users/**/limit/**/3,1),4,5/**/and/**/'1'='2
The /**/ is used to bypass the WAF which filters space characters.
The union select 1 part just displays the number 1 circled in red.
The brackets ( ... ) are used syntactically to prevent the DBMS from misunderstanding the limit part, as limit 3,1,select and as limit 3,1,4,5, which would both be incorrect without the brackets.
The limit 3,1 part means after the third result, output the next one, so it gets one name and one password, circled in blue.
Provided my understanding above is correct, I cannot understand why the tutorial author included the 4,5 part, nor why they included the '1'='2 part which evaluates to false?