When I submit an Customer Reference ID in an Android Application it POSTs an Encrypted String to an API Endpoint.
For example, if I enter the following CR ID :
"CR-13261150"
it POSTs the following Encrypted Data:
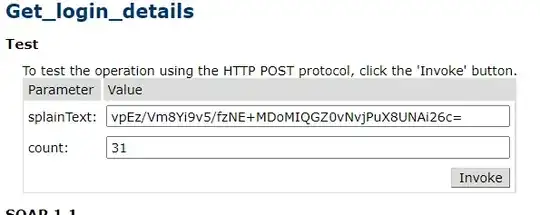
splainText : "vpEz/Vm8Yi9v5/fzNE+MDoMIQGZ0vNvjPuX8UNAi26c="
Count : 31
i can say count is based on Length of Customer ID,if the lenght is 11 then count is 31. (But All Valid Customer ID will have Length 11 for Sure)
Now let's assume if I submit the same CR ID in the following minute the Encrypted String Changes. But if I submit the same CR ID in the very same minute then for some reason I get the very same Encrypted String.
How do I find the encryption type and encryption method ?
I need help in decryption of the below encryption string.
And in my Last Question 2 People Answered Almost Correct,But Question was not clear to solve it Completly. please see this : How to Find Encryption Type by Seeing Encrypted Text?
Below Sample Data are Captured by Postman Proxy:
| Input Text | TimeStamp # | Encrypted Text | Count |
|---|---|---|---|
| CR-1 | 2022-04-05 02:17 | 0okiX0NBe8ebCMxtugOESY/UL9q20YVp8TQKEMQdpFU= | 24 |
| CR-12 | 2022-04-05 02:17 | YfsK2i1KKN/2eWmTOs43Tm+hKK+fjN41Z3++Lq+s4q8= | 25 |
| CR-123 | 2022-04-05 02:17 | oKDqXZ6LnLrfhQLzbxX9xRxsYZe5lxuMm79HAVm1fiQ= | 26 |
| CR-1234 | 2022-04-05 02:17 | oj6mQ0dFnX3TsUfMbohfu/vc9vUAX+CIuj7kcVBqV4c= | 27 |
| CR-12345 | 2022-04-05 02:17 | ksOZKdIif+su7zFoWIhpHqzlDWspUIiiUK2gyQ1rhPs= | 28 |
| CR-123456 | 2022-04-05 02:17 | pZTWTBKIn5KwNS0xw+mkW1GyG1agA67GWoAiHgDNcjY= | 29 |
| CR-1234567 | 2022-04-05 02:17 | cbnGD2N8e/rFo/2FebCfCOkThkTVLUyCpbw2YAIErAM= | 30 |
| CR-1234568 | 2022-04-05 02:17 | dMniBANrtzK48iDPGeI59nRkOA47t7WUU73osxbtowA= | 31 |
| CR-13261150 | 2022-04-04 22:40 | vpEz/Vm8Yi9v5/fzNE+MDoMIQGZ0vNvjPuX8UNAi26c= | 31 |
| CR-13261150 | 2022-04-04 22:42 | vpEz/Vm8Yi9v5/fzNE+MDvJkkl9i6iF/gg++QsHKTfM= | 31 |
| CR-13261150 | 2022-04-04 22:43 | vpEz/Vm8Yi9v5/fzNE+MDm1b+GWmC51UdhcUXD5Hjmw= | 31 |
| CR-13261150 | 2022-04-04 22:44 | vpEz/Vm8Yi9v5/fzNE+MDsKjpyLB7YvaJhNqqhlCHmU= | 31 |
| CR-13261150 | 2022-04-04 22:45 | vpEz/Vm8Yi9v5/fzNE+MDgNkvZYustpcpgQ0Aaj/dxc= | 31 |
| CR-18138469 | 2022-04-04 22:54 | S5uLpQfVT8C4GRCoQTDL+1ENt2lNa7+Rra/gvAx97zQ= | 31 |
| CR-18138469 | 2022-04-04 22:55 | S5uLpQfVT8C4GRCoQTDL+xuUFO0Si0cGYQL8WCo5Sxg= | 31 |
| CR-18138469 | 2022-04-04 22:56 | S5uLpQfVT8C4GRCoQTDL+y6puq8h6V0N326T/BMr+p4= | 31 |
| CR-18138469 | 2022-04-04 23:01 | S5uLpQfVT8C4GRCoQTDL+/nZFmv3EYRdC8iG66mfgD8= | 31 |
| CR-26752464 | 2022-04-04 23:05 | fT7K9VSRWTTYCYF51PJA02GfRjfRY8c4K1V5CptfHCs= | 31 |
| CR-26752464 | 2022-04-04 23:06 | fT7K9VSRWTTYCYF51PJA024r3eotFDInICu99mzuuqI= | 31 |
| CR-26752464 | 2022-04-04 23:07 | fT7K9VSRWTTYCYF51PJA07SxLQrsVZGNNgF+Dv4f/Pg= | 31 |
| CR-22224896 | 2022-04-04 23:10 | 8slKBTMUBaSap9VrwL3YZ/WgR9hqauqTkg9RmKVeHCI= | 31 |
| CR-22224896 | 2022-04-04 23:11 | 8slKBTMUBaSap9VrwL3YZw/dAhQtMzpsas1T5A8SJiU= | 31 |