I've recently set up a mitmproxy on my phone and it seems to work fine. It intercepts that request for https websites and I can view their content.
But I'm trying to intercept data from a banking app I have on my phone. The connection works perfectly fine and I can see all of the requests that get sent from my phone on the console. Except I don't know how to make sense of the response or the payload. It looks a bit like it's encrypted but I'm not sure if it is.
Can the data still be encrypted even though I've installed the mitm cert and am able to view other https responses and payloads?
Updated
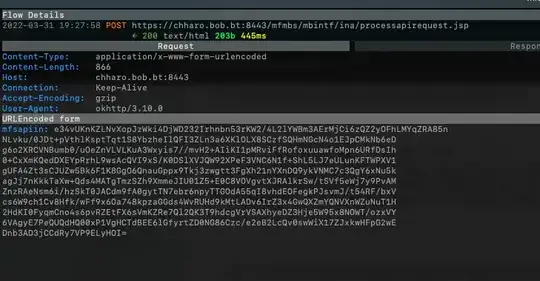
As pointed out by schroeder and Robert, the response is likely encoded rather than encrypted. After going through the common encoding algorithms: gzip, deflate, and trying to decompress the payload, I'm unable to figure out which encoding was used for this. Here are some screenshots. I was wondering if someone could point out possibly what encoding was used or whether I'm still stuck with the XY problem.