When I am testing mutual TLS handshake performance on TLS1.3 using OpenSSL, I find a very wired thing:
I created two groups of servers and clients:
- Server1 has a certificate signed using RSA3072, and Client1 has a certificate signed using ECDSAP256
- Server1 has a certificate signed using ECDSAP256, and Client1 has a certificate signed using RSA3072
In theory, the handshake performance for Group 1 and 2 should be roughly the same because:
- both combinations should generate one RSA3072 and one ECDSA256 signature for CertificateVerify.
- both combinations will verify two RSA3072 and two ECDSA256 signature.
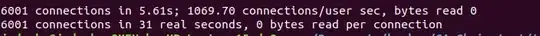
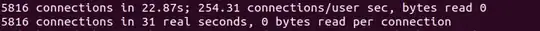
However, the test result is different. The handshake setup speed of Group1 is much faster than Group2.
According to algorithm performance, the verify speed of RSA3072 is slightly faster than ECDSAP256 but its sign speed is much slower than ECDSAP256. Therefore, I suspect that the CertificateVerify message from the server is not generated during the handshake process.
I am very confused about this guess because, in the tls1.3 IETF, it says that:
CertificateVerify: A signature over the entire handshake using the private key corresponding to the public key in the Certificate message.
The CertificateVerify is generated based on the handshake information so it should be generated during this process.
My questions here are:
Is there any error in my test and my guess?
If my guess is right then when does the server generate the CertificateVerify message?
More Clarification:
The certificate chain is generated by my own using the openssl command and the root certificate is self-signed.
For the testing, I used s_server and s_time to test the performance. I also used s_client with -msg to trace the process of the handshake. The certificate verification happened and the CertificateVerify messages for both server and client are sent.