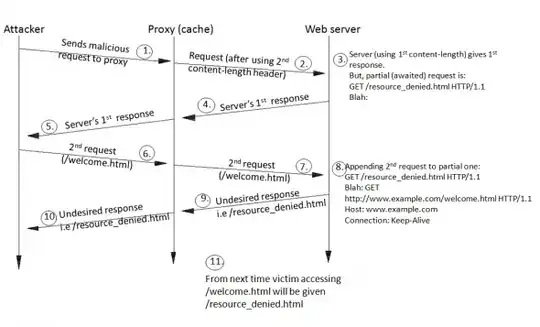
I am not going into basics of HTTP response splitting attack as above figure completing describes the working of such a attack. Previous Post have also discussed working of such a attack ASP.NET HTTP Response Splitting Attack.
My question rather confusion is that there exist a view in the community that such attacks are no longer possible and are mitigated by the underlying framework. What are the mitigation strategies? are they client side or server side etc. I also find lack of authenticated reference in this regard.