To answer your question I'm going to need to lay some groundwork.
Both SRAM and DRAM are volatile memory technologies, meaning that when you power them off they lose state. SRAM stands for Static Random Access Memory, and DRAM stands for Dynamic Random Access Memory.
SRAMs are static memories. The word static in this context means that once you have established a particular state, it will not change until you purposefully alter it, as long as power is present. DRAMs are dynamic, meaning that they will not permanently hold their state, even if power is present.
SRAMs are constructed from two cross-coupled inverter circuits. An inverter outputs a logical 1 (high voltage) if its input is a logical 0 (low voltage), and vice versa. By placing two inverters in parallel, in opposite directions, they hold whatever state you have applied:
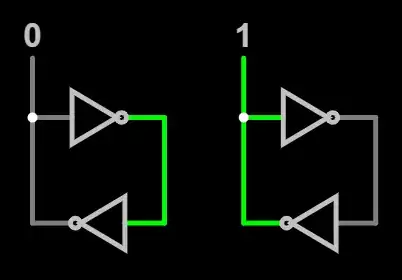
The input is used to pull the circuit into one state or the other. If you disconnect the input, the inverters keep holding the same state - if the left side is 0, then the top inverter sets the right side to 1, which causes the bottom inverter to set the left side to 0, and it remains in that equilibrium. The same happens in reverse if the left side is 1 and the right side is 0. The circuit will maintain its state until you "pull" it into a different state.
In practice, when building SRAMs out of transistors on silicon, we usually use a topology called a 6T SRAM cell:
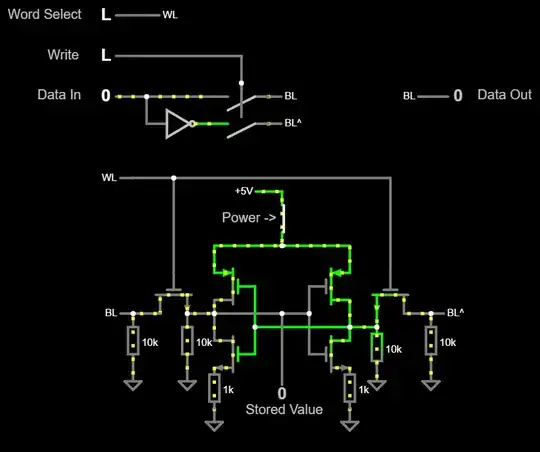
This is called a 6T cell because it uses 6 transistors. You can play with a simulation of a 6T cell here. Click on the inputs (left side) to change their values.
The word select (WL) line enables access to a cell. When WL is low, all other inputs are ignored. If you set WL to high, the data that is stored in the cell will appear on Data Out. If, while WL is high, you strobe the write signal, the value that is present on Data In will be written to the cell. When WL goes low again, the cell still remembers its value. You can wait as long as you want and the value won't go away. However, if you disconnect the power (switch in the middle) the cell instantly loses its state. There is no data remanence with an SRAM cell - disconnect the power and the data is gone.
DRAMs work very differently. In a DRAM, you use just a single transistor. I went deep into the gory details of DRAM construction here if you want to know more about it, but I'll present a simplified version here:
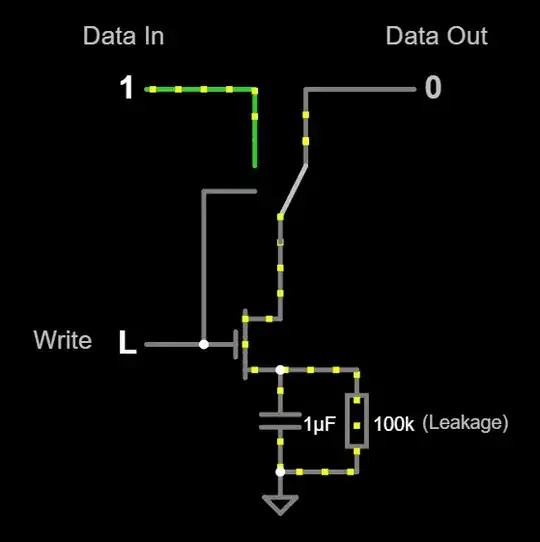
Simulation link.
This simplified version is missing all the logic for enables and column/row selection that you'd find in a real DRAM, but it's enough for this demonstration.
A DRAM works by keeping the cell's value in a capacitor. If the capacitor is charged, that represents a 1. If the capacitor is discharged, that represents a 0. If you set the data in, then strobe the write signal, the value is stored in the cell. In this simplified circuit, the value immediately appears on the output.
However, unlike with the SRAM, if you try setting a 1, then wait, you'll find that the data out eventually drops to 0. This is because of leakage. Capacitors aren't perfect, so they slowly leak charge out of them over time. If left alone, the states of the DRAM cells will degrade.
We solve the leakage problem by "refreshing" the cells. There are two key types of DRAM refresh operation: opportunistic, and manual. An opportunistic refresh is performed every time a cell is read. When a DRAM chip is asked to read a page of data, it activates the necessary DRAM cell and reads its value to a small internal SRAM buffer. This SRAM buffer is used to keep a temporary copy of the current data being read. The data is put onto the data bus so that the CPU can read it. The data is then also written back from the SRAM buffer to the DRAM cell, to recharge the capacitor back up to full if the data is a 1, thus undoing any leakage that occurred in the meantime. However, many pages of memory will not be read very frequently. DRAM memory controllers have a built in set of logic to constantly keep track of every page it hasn't touched in a while and send occasional refresh commands for them. The refresh command is just like a read, except the data is just read from the cell to the buffer and written back, internally on the DRAM chip, rather than being transmitted back to the CPU.
Here's a simple example of a buffer (the triangle component on the top right) being used as part of a cell refresh scheme:
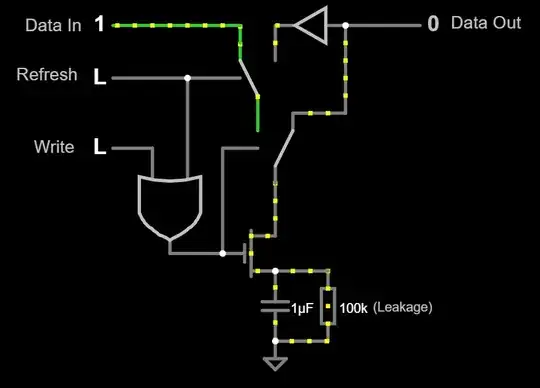
Simulation link
In practice the buffer would be an SRAM that is written to, then written back, but the circuit above shows how the concept works. When a refresh occurs, the data that is in the cell is read as a 1 or 0 (rather than the exact voltage of the capacitor) and that value is then written back to the cell. In the case of a 1, that recharges the capacitor back to full.
So, why do we use one or the other?
SRAMs are much simpler to use - they typically have an address bus that selects the particular set of cells to be read/written, a data bus that the CPU can put data on for a write, and that the SRAM can put data on for a read, and strobe signals for read and write operations. They can be used by low-speed microcontrollers and CPUs because they're static and don't need refreshing. Many SRAMs are asynchronous, which means the read/write operations occur whenever the read/write signals are strobed.
DRAMs are far more complicated to use. They, too, have an address bus and a data bus. However, they also have a more complex access scheme that uses columns and rows, requiring pages to be opened and closed. Many DRAMs are synchronous (referred to as SDRAM), meaning that they use a clock signal to synchronise all of the signals coming in and out of the memory IC. SDRAMs often use a command bus rather than individual read and write strobe signals. The device that controls the DRAM must constantly keep on top of refreshing the pages that have not been recently read. This makes them only suitable for fast processors and FPGAs.
The problem with SRAMs is that they don't scale very well. Each cell is large, requiring 6 transistors in a 6T cell topology. There is another topology called 4T, which replaces two of the transistors with resistors to make the cell smaller, but that comes with a significant power consumption tradeoff. This means that you can't build very large SRAMs, at least not cost effectively. They typically top out at around 128Mbit or so in size, and become quite expensive at that size if you want them to be fast too.
DRAMs are more complicated, but each cell can be made very small. This allows them to scale to much larger sizes. Modern DRAM chips can store a gigabyte or more of data. While SRAM cells are technically faster, the larger number of DRAM cells that can be packed into an area allows the memory bus width (i.e. number of bits read/written per access) to be much larger, thus leading to far greater memory bandwidth overall.
Computers (PCs, Macs, phones, etc.) don't use SRAMs for their main memory, and haven't really since the 80s. The early IBM PCs used asynchronous DRAM, and used a dedicated external microchip (Intel 8203) to handle DRAM refresh operations. Later we moved to synchronous DRAMs, i.e. SDRAMs, which were commonly used in early Intel Pentium systems.
You're probably most familiar with RAM that looks like this:
Above is an SDRAM stick. Each chip is an SDRAM IC, and the computer has a memory controller that talks to all of those chips over the memory bus.
A later iteration of the SDRAM technology was to have the data bus transmit on both the rising and falling edges of the clock signal, for twice the data rate. This was called Double Data Rate, or DDR. This standard has continued until today, with DDR2, DDR3, DDR4, and DDR5 SDRAMs being near-universal standards.

That brings you up to speed with the tech. Main system memory, where all your programs keep their working data, is a DRAM. SRAM is not used for that purpose.
That's not to say that there aren't SRAMs anywhere inside a modern computer - to the contrary, there are probably hundreds of millions of SRAM cells throughout the devices in a modern computer - but they're not what you'd consider "RAM". It's important not to think of these memory technologies as discrete chips or computer parts, but as actual pieces of electronic technology that can be used in the silicon of processors, memories, and other ICs.
Now, let's talk about security.
The primary security concern with DRAMs is a cold-boot attack. If you freeze a DRAM chip, the leakage current of the capacitors in the DRAM cells drops considerably. This can give you time to unplug the memory module from the computer and plug it into a specialised system for reading the contents, before the contents of the memory cells inside the DRAM decay. This attack is a concern because modern computers use DRAM as their main memory, and those DRAM chips are on a removable module.
The same attack does not hold for SRAMs. First, the cooling part is pointless - SRAMs lose their data the instant they lose power. There's no capacitor to reduce the leakage current of. But, you might say, we can just keep the power connected to the SRAM! And then it won't lose any data because it's static! Well, yes, technically, but that's where we get to problem two: what SRAM? There's no removable SRAM memory stick on a modern computer. The SRAMs that exist are memories and buffers inside the silicon of the CPU, the PCH, the Ethernet PHY, the GPU, the SuperIO, the USB controller, the VRM controller, and other ICs on the motherboard. They don't store the program memory. They're single-purpose buffers used for managing internal state. The blocks of SRAM in the CPU (e.g. buffers and caches) will potentially contain sensitive data while the CPU is working on it, but how're you going to access them? If you've got the capability to decap a running x86_64 processor and tap the ten-or-fewer nanometer wide transistors to get at this data, you could've just bought a commercial memory forensics solution that uses a DDRx interposer to read the main system memory.
The battery on the motherboard is used to keep the realtime clock running. In the ye olden days, it also used to power the "CMOS", which is a misnomer and actually a little discrete SRAM chip. That chip contained the BIOS settings. They used a non-volatile memory with a battery backup because it meant that you could always zero out the whole thing by pulling the battery, allowing you to reset the settings to default even if they'd become corrupted and the system wouldn't boot. These days it's common to use an EEPROM instead, which is non-volatile, and have a supervisory circuit that can zero it out. It doesn't contain any information about the programs that are running on your computer, though. It's specifically just for BIOS settings. The bus on it is low speed, so it doesn't matter whether it's an EEPROM or an SRAM - you can just solder wires onto its pins and sniff the data as it's read/written at any time.
Other SRAM blocks inside other ICs have the same issue as with the CPU. They're on the silicon, not separate physical chips, so you can't really get at them.
So yeah, that's about it. SRAMs aren't used for system memory, so the attack you describe doesn't really exist.





