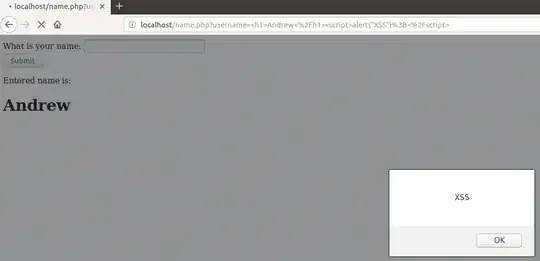
Have they hardcoded the username and password on the JSP page?
Yes, they did.
Before submitting the bug to the site owner, how can I test the information exposure and "exploit"?
No need to test anything. It's right on the source code of the site, so I doubt any further proof is necessary.
What is the best way to prevent such instances besides following OWASP Top 10?
There are some relevant OWASP entries:
Security Misconfiguration: a production server should not be configured in such a way that errors with debug messages got sent to the clients. This allows an attacker to enumerate products, versions, and possible vulnerabilities. In this specific case, even database access credentials.
Software and Data Integrity Failures: "Software and data integrity failures relate to code and infrastructure that does not protect against integrity violations."
Database access should be handled by a software component (for the lack of better definition) that should handle, among other things, exception handling and log generation. In this case, there's no exception handling at all and the log is sent to the client.
Identification and Authentication Failures: "Uses plain text, encrypted, or weakly hashed passwords data stores."
Cryptographic Failures: "... previously known as Sensitive Data Exposure, which is more of a broad symptom rather than a root cause, the focus is on failures related to cryptography (or lack thereof). Which often lead to exposure of sensitive data. Notable Common Weakness Enumerations (CWEs) included are CWE-259: Use of Hard-coded Password, CWE-327: Broken or Risky Crypto Algorithm, and CWE-331 Insufficient Entropy."
In this case, CWE-259: Use of Hard-coded Password applies. It's more a sensitive data exposure than a cryptographic failure, but it's a failure anyway.
Is this DB publicly accessible now?
It depends. They leaked the username and password, so if someone manages to get network access (remote file inclusion, remote code execution, server-side request forgery, etc) it's possible to connect direct to the database.
This could be development code ending up in production, but this does not lower the severity of the issue. If this is the case, it shows the company does not have proper software lifetime standards in place, or don't even have development/staging/production environments.