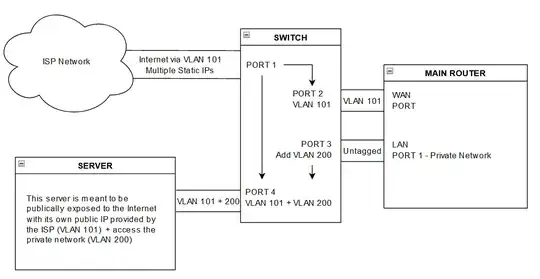
I saw a network setup recently that looked like the following:
The ISP provides two static public IPs on a specific VLAN and one is used for an internet network and the other for a server exposed to the Internet.
They wanted the server to have access to the internal network as well but without depending on the internal router - to avoid downtime due to internal network maintenance etc.
What they did was to use a Switch after the ISP ONT (Optical Network Terminal) that passes VLAN 101 to the router WAN port and to the server port as well. Then they connected one of the router's LAN ports to the Switch so it can tag all the traffic and make it available on the server port as well.
Questions:
1) Is this setup secure? How likely is for someone on the Internet to be able to access their internal network? Maybe using some kind of VLAN hopping attack? What about the ISP?;
2) The switch is a GS105Ev2. Can it really isolate the networks?
I know that the server can be hacked via its public IP and someone might use it to access the internal network, but le'ts assume that's not possible and strictly focus on the security implications of having a public and private network on the same cable and a setup like that.