I'm curious to know how mTLS works in more detail in regard to client authentication.
Firstly, I issued 3 certificates: root CA, server and client. The last two are signed with the root CA.
Secondly, I imported the client's .p12 (the client certificate and the private key incorporated) and the root CA (certificate only) to my KeyChain.
Finally, I configured nginx on my localhost with SSL enabled and set the server certificate and the private key. I also set the rootCA as an "appropriate authority" for clients' certificates like so:
listen 443 ssl;
ssl_certificate /usr/local/etc/nginx/ssl/testcasignedsrv/x509-server.crt; // server's certificate
ssl_certificate_key /usr/local/etc/nginx/ssl/testcasignedsrv/x509-server.key; // server's private key
ssl_client_certificate /usr/local/etc/nginx/ssl/testcasignedsrv/ca.crt; // self-signed CA that signed the client's and server's certificates, "CSU" in this case
ssl_verify_client on; // enables client's authentication
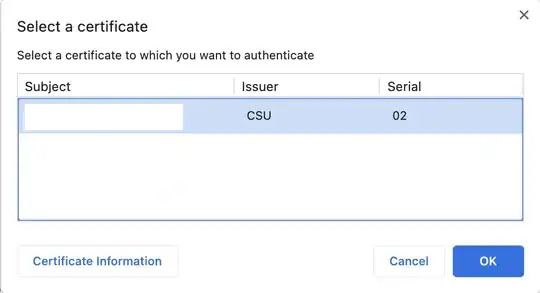
Everything seems to work fine since when I visit the localhost I'm presented with a pop-up to choose the certificate
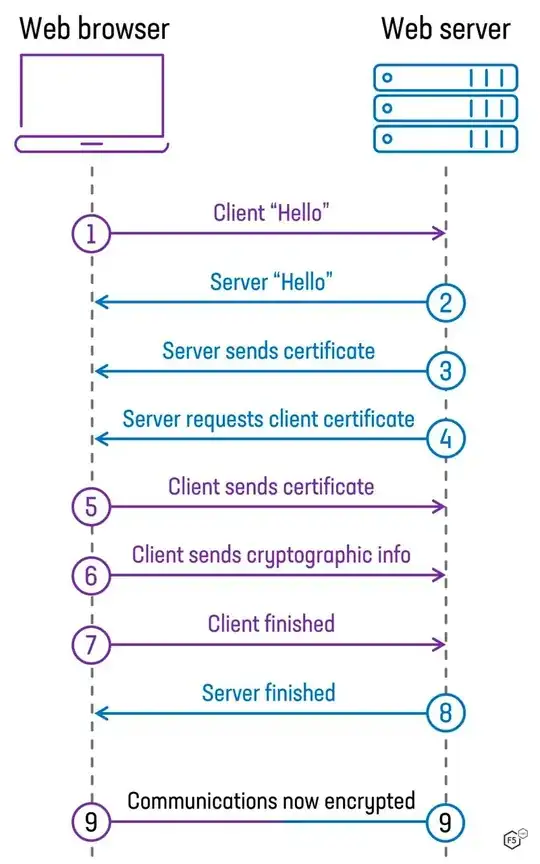
After I choose one, the authentication succeeds in accordance to the following mTLS figure
As far as I understand, the client certificate is sent to the server, then the Signature of the client certificate (the signature of the issuer inside the client certificate) is verified with the rootCA public key. If it matches, the client is allowed to the web-server.
My question is what do I need the client's public and private keys for in terms of mTLS? Maybe when I hit "OK" in the browser the client's own signature created (with the private key) and somehow verified with the root CA? Could anyone please clarify.