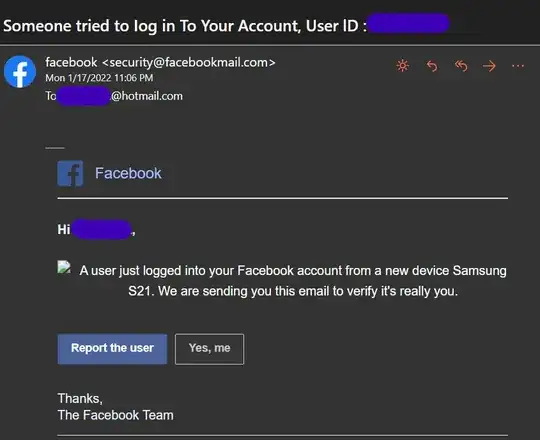
I received a strange email from security@facebookmail.com. Sources on the internet seem to state that this is a Facebook-owned domain but I know the email is not legit because they do not address me by my first name, but instead by my email address. Also, I do not have a Facebook account with this particular email address.
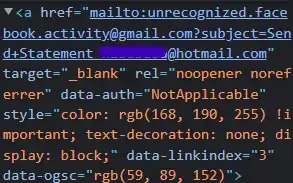
Scam emails like this typically include links to malicious websites. However, this one does not. The main action button of the email is a link to send an email to unrecognized.facebook.activity@gmail.com, which is obviously not a legit Facebook email address. All of the other buttons and links in the email also have a mailto: link to the same address, just with a different Subject.
If it matters, the email client I was using is Outlook.com.
I have 2 questions regarding this.
1. How did it pass SPF, DKIM and DMARC?
I know that this question was asked before:
How did this paypal spoof email pass SPF, DKIM and DMARC
How did a phishing email pass SPF, DKIM and DMARC?
However, in the first case, it was an actual legitimate email. In the second one, the address was From: Bank Of America <peopledevelopment@uber.com>, so there was no actual spoofing. In my case, it is facebook <security@facebookmail.com>. There are no special characters.
2. How does the scam work?
It does not seem that clicking the links will cause anything malicious, since it will just create a new email in the receiver’s email client.
I found a similar question: Trying to understand the point of this scam email
Over there, the answers mention that it might be a way to generate the email addresses of people who do click the buttons. I do not see how this might apply to my example because the link does not actually send the reply email, but just creates it locally on the email client.
For comparison, this is what I see when I inspect the main button:
I tried to use the View Message Source feature on my email client, and found something interesting:
Received: from AM4PR0202MB2852.eurprd02.prod.outlook.com (2603:10a6:200:8e::8)
by AS8PR02MB6583.eurprd02.prod.outlook.com with HTTPS; Mon, 17 Jan 2022
21:06:19 +0000
Received: from MWHPR12CA0043.namprd12.prod.outlook.com (2603:10b6:301:2::29)
by AM4PR0202MB2852.eurprd02.prod.outlook.com (2603:10a6:200:8e::8) with
Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.4888.9; Mon, 17 Jan
2022 21:06:15 +0000
Received: from CO1NAM11FT028.eop-nam11.prod.protection.outlook.com
(2603:10b6:301:2:cafe::f4) by MWHPR12CA0043.outlook.office365.com
(2603:10b6:301:2::29) with Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.4888.10 via Frontend
Transport; Mon, 17 Jan 2022 21:06:14 +0000
Authentication-Results: spf=fail (sender IP is 31.192.237.146)
smtp.mailfrom=facebookmail.com; dkim=none (message not signed)
header.d=none;dmarc=fail action=oreject
header.from=facebookmail.com;compauth=fail reason=000
Received-SPF: Fail (protection.outlook.com: domain of facebookmail.com does
not designate 31.192.237.146 as permitted sender)
receiver=protection.outlook.com; client-ip=31.192.237.146; helo=brave19.com;
Received: from brave19.com (31.192.237.146) by
CO1NAM11FT028.mail.protection.outlook.com (10.13.175.214) with Microsoft SMTP
Server id 15.20.4888.9 via Frontend Transport; Mon, 17 Jan 2022 21:06:13
+0000
It seems that the email failed the SPF check? If so, how did the email end up in my inbox?