In the good old days, you made server-side websites using PHP or something like that, now we have modern web apps divided into front-end and back-end (usually API Rest), you can't rely on CORS because some clients like postman don't care about it.
How can you protect confidential info? picture this:
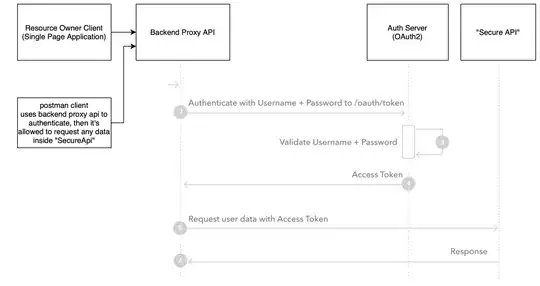
You have an API let's call it "Secure API", it uses OAuth2 grant flows, and has confidential data.
You have the resource owner client (Single Page Application with a backend (API Rest) to proxy the requests to "Secure API" and take charge of auth), but as I said before, anyone can hit the backend from something like postman and impersonate the client (I do not know if "impersonate" is the correct term).
How do you protect the communication between the backend and front-end?
Should we back to the good old days when dealing with sensitive data?
What alternatives do I have to connect with "Secure API" from the resource owner client?
EDIT: this graph explains the case I mentioned above
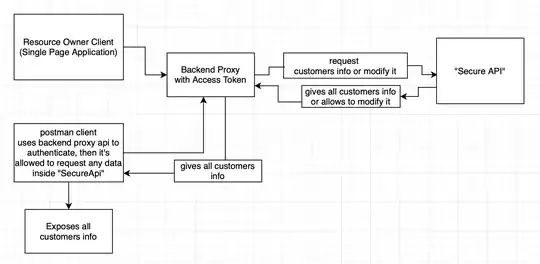
The thing is that I don't want to allow every authenticated client to get the info, just the Resource Owner Client, is there a way to do that?
I haven't designed the API it's just a hypothetic case, but here is an example
Backend proxy access token has all the permissions, because its intended to be used only by the resource owner client