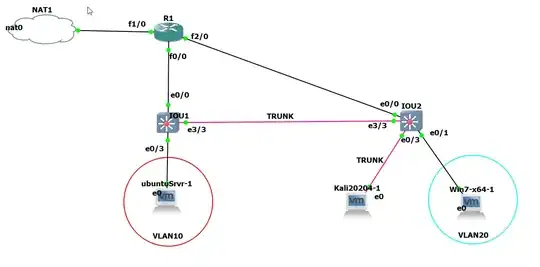
In the below scenario, I'm using Yersinia for VLAN Hopping through switch spoofing. Steps are:
eth0 on kali is unset.
runing Yersinia and launch a DTP attack (Sending DTP packet or Enabling trunk method)
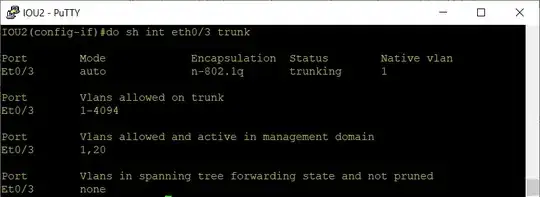
Check if eth0/3 (switchport) becoming trunk
Launch wireshark on kali machine to see traffic going between vlan10 and vlan20
Ping win7(vlan20) from ubuntuSrvr(vlan10)
in the result of attack interface eth0/3 goes to trunking status,
but wonder why I cannot see the traffic between Win7(vLAN20) and ubuntuSrvr(vLAN10) in wireshark??
Note: wireshark is running in kali machine (attacker machine).