This approach to data destruction is theatrical and has little grounding in reasonable threat models.
The most effective policy to ensure safe and responsible disposal of SSDs is:
- Use full-disk encryption (e.g. BitLocker, dm-crypt) for the whole lifetime of the disk, and do not write plaintext data to it.
- Utilise ATA Secure Erase to wipe the disk. Modern SSDs have transparent encryption at the cell level, and ATA Secure Erase simply discards the key and generates a new one. This renders the data on the underlying flash unreadable.
- If you are paranoid, perform a single-pass random wipe over the SSD afterwards. This is rarely justifiable in practice, and is not a safe sanitisation practice on its own due to flash wear-levelling and overprovisioning. It also causes wear on the flash cells, which is why Secure Erase exists in the first place.
If you're already at the point where you're disposing of the disk, and you forgot step 1, then you're in a worse position than you could be, and this is a lesson for next time.
Regarding step 3, the thing about performing random wipes on SSDs is that it is only justifiable if you're trying to gain additional protection against flawed Secure Erase implementations. However, this only makes sense if you presume that the ATA Secure Erase key cycling implementation is the only security boundary preventing an attacker from reading your data, and that an attacker will attempt to perform chip-level data recovery on your disk. Consider the following:
- If you're using FDE, you've already got a concrete layer of protection, so even if Secure Erase completely fails you don't need to worry about it all that much. But if you use ATA Secure Erase and you can't see the data on the drive any more, that means it did something, at least, which is good enough.
- Regardless of whether or not you're using FDE, if you're a regular person, attackers who have the capability to attack ATA Secure Erase implementations aren't interested in you, and do not stand to profit from using those capabilities on you, so you don't need to worry about it as long as the key is changed to literally anything else (if it wasn't, you could still see all your data).
- If you work in the type or organisation (government) where such an attack is relevant, you're already using FDE, and you're not getting your advice on StackExchange, so none of this is relevant to you and this entire answer is moot.
Whichever way you look at it, ATA Secure Erase is secure enough for an average person or business even if it is not implemented in a cryptographically secure manner. For it to fail as a wiping mechanism, it either has to do absolutely nothing (which is immediately obvious, because the data will still be there), or an attacker has to reverse engineer the SSD firmware, discover the weak key generation mechanism, and perform chip-level data recovery to leverage that attack. As we already established, no such attacker exists in the average person's threat model.
This is not the same as saying "everyone should just go with 'good enough' security all the time and not bother with more advanced mitigations" - that is obviously bad advice. What I mean is that any security decision you make that results in cost or waste should be justified and proportional to the security benefit.
Physical destruction of storage media is rarely necessary, highly wasteful, and should be reserved for scenarios where threat modelling demonstrates a significant safety risk. Many governments (and businesses) have operated excessively paranoid so-called "data destruction" policies for the past decades, but have more recently re-assessed their approach due to the extreme overheads involved.
The historical practices of multi-pass wipes, including utterly ludicrous 35-pass methods, are without merit on modern storage media. At best they do nothing more than wear out the storage device, and at worst they do not effectively remove sensitive information from the device (e.g. due to overprovisioning and wear levelling). Peter Gutmann himself, who wrote the paper that spawned the "Gutmann method", has this to say on the topic:
In the time since this paper was published, some people have treated the 35-pass overwrite technique described in it more as a kind of voodoo incantation to banish evil spirits than the result of a technical analysis of drive encoding techniques. As a result, they advocate applying the voodoo to PRML and EPRML drives even though it will have no more effect than a simple scrubbing with random data.
In fact performing the full 35-pass overwrite is pointless for any drive since it targets a blend of scenarios involving all types of (normally-used) encoding technology, which covers everything back to 30+-year-old MFM methods (if you don't understand that statement, re-read the paper). If you're using a drive which uses encoding technology X, you only need to perform the passes specific to X, and you never need to perform all 35 passes. For any modern PRML/EPRML drive, a few passes of random scrubbing is the best you can do. As the paper says, "A good scrubbing with random data will do about as well as can be expected".
This was true in 1996, and is still true now.
Highly disproportionate and extreme approaches to data destruction gained popularity after the DoD 5220.22-M standard was declassified, which was quickly exploited by vendors of disk wiping software to market their products as "military grade". However, people who were involved in the DoD data destruction standards later admitted that almost none of it was scientifically justified, and was instead written with the goal of appeasing military paranoia and gaining buy-in from non-technical higher ups - hence why it was named "data destruction", rather than "media sanitisation".
The excesses of past policies ultimately resulted in a reduction of security posture through security fatigue and avoidance of onerous requirements. More modern standards recognise this, and take a far more scientific approach.
For media sanitisation I recommend reading and following the advice in NIST SP 800-88 Rev.1. It is very accessible and provides clear advice specific to each type of storage technology. Appendix A contains the most quickly digestible portion of the advice, but you should refer to the guidance in section 4 of the document with regard to which media sanitisation approach you take. Section 2 also provides useful background information.
It is extremely difficult to justify physical destruction of storage media for any regular citizen. To be blunt, it is delusional to expect that a threat actor exists that has the technical capability to perform flash-level data recovery, the motivation and resources to utilise that capability effectively, and proportional motive to justify targeting your data specifically. Unless you're a political dissident or organised criminal, these scenarios are pure fantasy. If you are in one of those groups of interest, extreme approaches to data destruction are bad for operational security because they draw unnecessary attention.
I recommend reading James Mickens' This World Of Ours for a wonderfully humorous take on misguided and overly convoluted security practices:
In the real world, threat models are much simpler. Basically, you’re either dealing with Mossad or not-Mossad. If your adversary is not-Mossad, then you’ll probably be fine if you pick a good password and don’t respond to emails from ChEaPestPAiNPi11s@virus-basket.biz.ru. If your adversary is the Mossad, YOU’RE GONNA DIE AND THERE’S NOTHING THAT YOU CAN DO ABOUT IT. The Mossad is not intimidated by the fact that you employ https://. If the Mossad wants your data, they’re going to use a drone to replace your cellphone with a piece of uranium that’s shaped like a cellphone, and when you die of tumors filled with tumors, they’re going to hold a press conference and say "It wasn’t us" as they wear t-shirts that say "IT WAS DEFINITELY US," and then they’re going to buy all of your stuff at your estate sale so that they can directly look at the photos of your vacation instead of reading your insipid emails about them.
Attempted destruction of an SSD with a lighter is a perfect example of theatrical security policies that feel secure without actually doing anything useful. To destroy an SSD with heat, you generally need to heat them to a temperature far in excess of what a simple lighter can provide. Even if you heat the flash memory ICs directly, much of the heat you're applying to the package will be dissipated by the leadframe and component legs, meaning that the die temperature will be far lower than that of the flame.
It is also important to understand that data retention in flash cells at high temperatures is not best modelled by a "failure point". The behaviour is better modelled as a degradation factor. Flash cells do not have an infinite storage lifetime while unpowered - over time, the cells will start to lose their state. The period between the last powered operation and the time at which the cells lose enough of their state to result in data corruption is known as the data retention rate. For most consumer SSDs, the retention rate is usually around a year, when the drive is stored at the recommended temperature range.
The degradation factor is the measure of how much faster the degradation occurs at a particular temperature. In the recommended storage temperature range, the degradation factor is close to 1. A degradation factor of 2 means that the data degrades in half the time. As the temperature rises, the degradation factor increases. The exact degradation factor at a given temperature is device-specific. For NAND flash, you should expect to see a graph similar to the following:
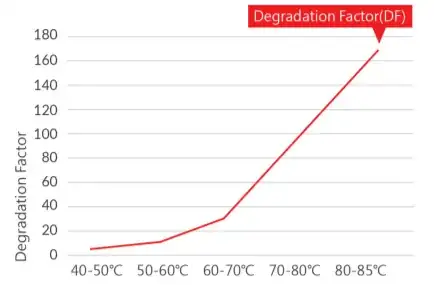
(source: Achieving Extensive Data Retention in High-Temperature Environments)
As the die temperature hits 80°C, the degradation factor exceeds 150. If the storage device under test has a standard retention rate of one year, a degradation factor of 150 reduces this to around 60 hours.
If we take a crude linear extrapolation of this graph, beyond the 60°C point, we get a gradient of around 6/°C. If we presume that your lighter manages to get the die temperature to 500°C, this would produce a DF of around 2100. Dividing one year by 2100 gives us 4.2 hours, which is a rough guesstimate of how long you'd have to hold the flash chip over your lighter before it degraded to a significant level. If we're a bit more charitable and assume that your lighter can heat the chip to 1000°C, that brings the degradation factor up to 5850, which still means an hour and a half of heating. Per flash chip. To get an equivalent degradation to one year of being powered off, which does not mean complete loss. This is obviously not practical. If we go all the way up to high-heat butane lighters, and assume that none of the heat is dissipated, we get to about 1900°C in a tightly focused flame - far greater than that of a blowtorch. The DF stops being relevant here because the copper will melt, but if it was still relevant you'd need to heat it for around 46 minutes. Still, this does rather prove the point that it takes a whole lot of heat and/or time to make this kind of destruction approach useful.
Putting a nail through the chips is certainly effective, but at a cost that makes absolutely no sense. If your SSD has failed to the point of being non-functional, and it still contains sensitive data (especially if you forgot to use FDE), sure, subject it to whatever physical destruction approach you like. Realistically, if you throw it away, nobody is going to try to read it by doing anything more than plugging it into a computer. There's no harm done in smashing up an already broken drive, other than the potential for injuring yourself in the process. It might even be cathartic. But if you physically destroy a functioning drive, you're just generating e-waste and costing yourself money for no tangible benefit.

