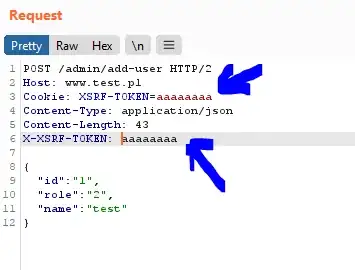
I have the Angular application where CSRF protection is implemented using Cookie-to-header token. It is default AngularJS mechanism to counter CSRF, which uses cookie XSRF-TOKEN and header X-XSRF-TOKEN. Only JavaScript that runs on my domain can read token from cookie and send it inside header, so it is the header that provides the protection. So it looks like stateless CSRF protection, where server does not safe and verify token correctness.
But someone reported as a vulnerability that server does not verify token correctness and it is possible to send arbitrary value in cookie XSRF-TOKEN and header X-XSRF-TOKEN and as long as both values are the same server accepts the request.
Is it really a vulnerability? At the first time reading this I thought that it is mistake and that is the way how this mechanism works, but in Angular documentation (https://angular.io/guide/http#security-xsrf-protection) I found this:
To take advantage of this, your server needs to set a token in a JavaScript readable session cookie called XSRF-TOKEN on either the page load or the first GET request. On subsequent requests the server can verify that the cookie matches the X-XSRF-TOKEN HTTP header, and therefore be sure that only code running on your domain could have sent the request. The token must be unique for each user and must be verifiable by the server; this prevents the client from making up its own tokens. Set the token to a digest of your site's authentication cookie with a salt for added security.
Does this mean that server should remember token value for every user and verify this value and do not accept requests like on the screen above?