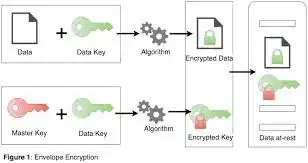
I need to encrypt personal data like email, phone number, etc. I am using AWS KMS for managing the encryption keys. This is the system that is already implemented is as follows:
- All the existing data is encrypted using a worker which first generates a data key by calling the aws-sdk. This call returns the plaintext(decrypted data key) and the encrypted data key. This plaintext is then used to encrypt the data and then is removed from the memory.
- Now whenever a new data key is generated, the encrypted data key is stored in a .json file and uploaded to AWS S3 bucket. This upload has Server Side Encryption enabled using a Customer Key. I store the path to this json file to the db table that keeps record of the active data keys.
- Whenever I need to decrypt data, I get the json file from the s3 bucket which contains the encrypted data key. Then I call the decrypt function of aws sdk and retrieve the original data key which is then used to decrypt the encrypted data.
Now my question is:
How do I manage the customer key used in step 2 for the server side encryption of the s3 file upload. Right now I generate a random key for each data key and store this in the data keys table. Is this a safe way to handle this key?
What is the general practice regarding using SSE-C keys? Should I keep a constant key for each data key instead of generating a new one?
any help is highly appreciated