Goal
- Authenticate the Client via HTTP Request.
- Authenticate the Client's WebSocket connection.
- Prevent exploitation of WebSocket connection(when a XSS Vulnerability is present on website).
How I'm doing this
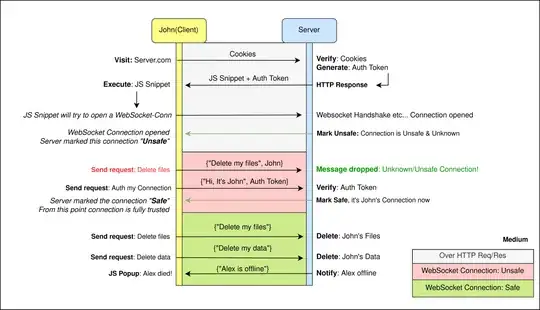
Step 1 Client visits the website by making a regular HTTP request. Cookies are used to authenticate the Client and server responds with a JS snippet + AuthToken(Generated & Saved at Server):
(function() {
var ws = new WebSocket("wss://localhost:1000");
// application logic goes here
})();
Step 2 Server marks newly created WebSocket connection as Unsafe/Unknown. Client has to send AuthToken via that Connection. Server will mark the Connection safe once it receive as valid AuthToken from any active WebSocket connection.
Overview of both steps
Things I'm enforcing
AuthTokenis short-lived(Expirable & One-time).- Encrypted transport, using
WSSprotocol Originis checked by the server header during WS handshake(To prevent CSWSH).- Server will process only messages that are sent over Safe marked connections.
Assumptions in the case of XSS Vulnerability
- WebSocket object
ws(created in the start) cannot be tampered with. - Attacker cannot create an Authenticated connection without
Cookies.
I want to know if above system is reasonably secure against XSS?