For OpenSSL's command-line program (openssl enc), the algorithm chosen also picks the key size (which is why they have separate options for aes-128, aes-192 and aes-256). They just don't have this option for Blowfish.
The enc program only supports a fixed number of algorithms with certain parameters. So if, for example, you want to use RC2 with a 76 bit key or RC4 with an 84 bit key you can't use this program.
openssl enc -bf always uses a 128 bit key:
Blowfish and RC5 algorithms use a 128 bit key.
The documentation for the Blowfish functions says you can use a variable-length key, so presumably if you wrote your own program compiled against OpenSSL, you could use whatever key size you want:
BF_set_key() sets up the BF_KEY key using the len bytes long key at data.
If you can choose your algorithm, and you want a longer key for whatever reason, OpenSSL will do AES with up to 256-bit keys: (openssl enc -aes-256).
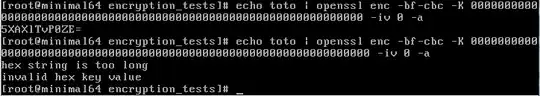
Given the above, you'd expect OpenSSL to complain when you go over 32 character (32 * 4 = 128), but it seems to silently ignore any data after the first 32 characters:
blong@ubuntu:~$ openssl enc -bf -iv 0 -P -K 000000000000000000000000000000012345
salt=0700000000000000
key=00000000000000000000000000000001
iv =0000000000000000
I submitted a bug report, because it looks like they're trying to catch this case, but the error is for > 128 characters instead of > 128 bits.