I use keepass to store my passwords and the keepassdx app to access that database on my Android phone. It offers the option to allow me to unlock with a fingerprint, if I set up fingerprint Auth on my phone.
Setting up fingerprints obviously means taking a scan, and I must assume that that scan, or some version of it, is then stored on my phone. The initial screen says about Knox which I believe is some sort of security layer/service of Samsung's.
I've always been against using biometric data because you can't change it, so if it's stolen you're in big trouble, proportional to the number of places you've used that data.
With trends towards webauthn and FIDO2 I feel like I'm wearing a tin foil hat by not giving my phone my biometrics. I'm unlikely to be the target of a well funded attack but I do need to be responsible with the data in my possession.
If like to understand
- how is the scan data stored - I've read that in 2015 some Samsung phones basically stored a bitmap image!
- does it leave the phone?
- does it mean Samsung (or Google!) have my fingerprints?
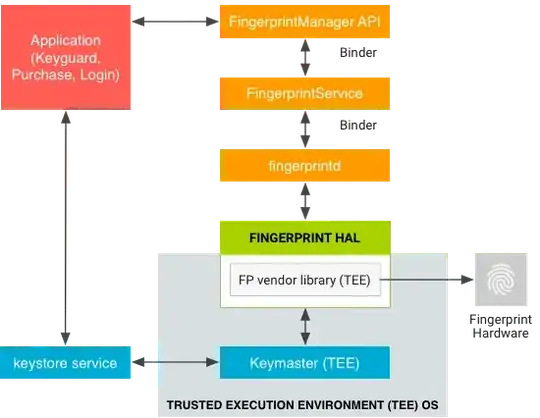
- how do apps interact with fingerprint scanners? Presumably apps don't get access to the print, but does each app get a unique key pair or something? Or does the API simply return a Boolean: yes authorised,or not.
- what is Knox's role? Why doesn't Android provide a native solution? Do I need Knox or would it be better to delete/disable it?