On the Evil Twin attack you use a rogue AP to imitate a genuine one by using the same SSID (so yes, answering to one of your questions, the SSID is going to be the same) however the Rogue AP usually does not implement any password and will probably have a captive portal that will lure the victim to write the password on it before proceeding:
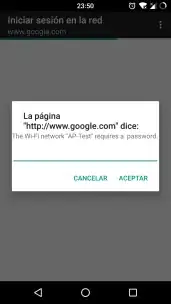
Evil Twin attacks may perform a de-authentication attack in order to force the users to re-connect, ideally with the Rogue AP.
I think that is very relevant to also bring some helpful answers that treated a slightly different question (but still related) and it is about how to protect yourself against EvilTwin attack:
Does WPA2 Enterprise mitigate evil twin attacks?
Since it looks like you encountered some troubles with this attack , if I had to choose a tool to perform an Evil Twin attack I would personally go for Airgeddon (https://github.com/v1s1t0r1sh3r3/airgeddon) which has a myriad of Evil Twin attacks, including:
- Only Rogue/Fake AP mode to sniff using external sniffer (Hostapd + DHCP + DoS)
- Simple integrated sniffing (Hostapd + DHCP + DoS + Ettercap)
- Integrated sniffing, sslstrip2 (Hostapd + DHCP + DoS + Bettercap)
- Integrated sniffing, sslstrip2 and BeEF Browser Exploitation Framework (Hostapd + DHCP + DoS + Bettercap + BeEF)
- Captive portal with "DNS blackhole" to capture wifi passwords (Hostapd + DHCP + DoS + Dnsspoff + Lighttpd)
- Optional MAC spoofing for all Evil Twin attacks
It is a super interesting suite well documented and made completely in Bash that is the reason why it is usually my first (and last) stop in terms of these attacks.
