I have a little Wordpress honeypot set up. I have it specifically set up so that when the server's IP address is accessed, the wordpress website shows up, ie. no vhost. I was reading the site's access logs and started noticing wordpress probes with the referer showing a strange website.
77.79.196.146 - - [10/May/2021:21:31:57 +0000] "GET /?author=2 HTTP/1.1" 200 3446 "http://faraday.xxxx.xxxx///?author=2" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0"
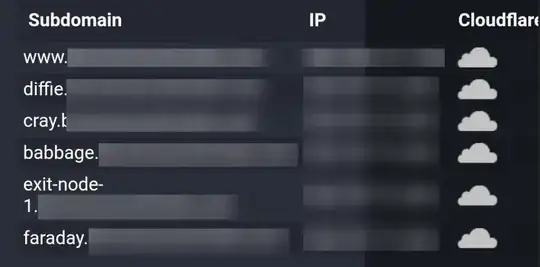
I decided to do a dns lookup of the site:
All of the site's subdomains (except for www which points to a GitHub pages IP) point to my server's IP address. Keep in mind this is a honeypot wordpress site that I haven't shared with anyone. I also have a domain attached to it (dns and rdns records). What is the point of this? This domain wasn't created to target me (or so I think), it was created almost three years ago.
What kind of attack is this and what is the attacker trying to achieve?