I'm trying to intercept and decipher scripted code that is sent to a previously installed Windows application, after a user have clicked on a particular URL in their web browser which is somehow returning a MIME response that is intercepted by the Win app and processed as a script/program.
The particular example of concern, is how the (Windows) trading application Think-or-Swim (aka. TOS) is downloading and running user scripts from either a custom URL handler of the form: tossc:XXXX or using a standard URL like http://tos.mx/A1PZUml which then sends one of the MIME types:
x-scheme-handler/tossc
application/x-tossc
application/x-thinkorswim
I have posted a similar question on SO here but I don't think that forum is appropriate for this question and hope someone here would a have some more technical know-how of how to do this and also explain what's going on. As you can tell I am probably not even using the correct language for asking the question in a clear manner. So feel free to correct me or this post.
Q: How can I intercept and inspect code that is loaded in this way?
(Hoping to also learn what is going on and how this is done, or an be done, by e.g. python?)
UPDATE: 2021-04-24
I managed to get some more info from using Process Monitor.
The settings should be something like this:
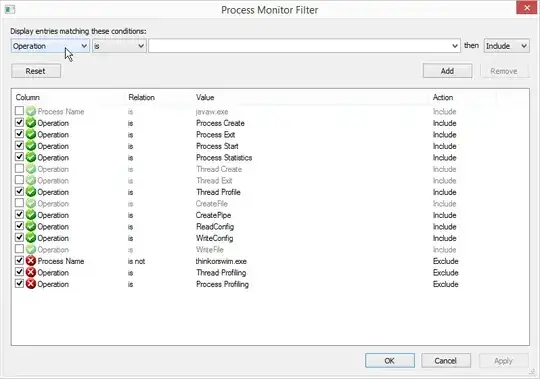
After than you can start ToS by clicking on the link button View in thinkorswim. The process table will then be filled and some of the interesting properties are:
"C:\Program Files (x86)\thinkorswim\thinkorswim.exe" SharedConfigurationLink tossc:A1PZUml
regsvr32.exe /s "C:\Program Files (x86)\thinkorswim\nptossc.dll"
regsvr32.exe /s "C:\Program Files (x86)\thinkorswim\npthinkorswim.dll"
regsvr32.exe /s "C:\Program Files (x86)\thinkorswim\lib32\RTDService.dll"
regsvr32.exe /s "C:\Program Files (x86)\thinkorswim\lib64\RTDService.dll"
C:\Windows\sysnative\reg.exe add HKEY_CLASSES_ROOT\tossc /ve /t REG_SZ /d "URL:TOS Sharing Center URL" /f
C:\Windows\sysnative\reg.exe add HKEY_CLASSES_ROOT\tossc /v "URL Protocol" /t REG_SZ /f
C:\Windows\sysnative\reg.exe add HKEY_CLASSES_ROOT\tossc\shell\open\command /ve /t REG_SZ /d "\"C:\Program Files (x86)\thinkorswim\jre\bin\javaw.exe\" -cp \"C:\Program Files (x86)\thinkorswim\suit\1968.2.0\tos-suit-1968.2.0.jar\" com.devexperts.jnlp.platform.impl.windows.WindowsSharedConfigurationLauncher SharedConfigurationLink %1" /f
C:\Windows\sysnative\reg.exe add HKEY_CLASSES_ROOT\thinkorswim /ve /t REG_SZ /d "URL:thinkorswim URL" /f
C:\Windows\sysnative\reg.exe add HKEY_CLASSES_ROOT\thinkorswim /v "URL Protocol" /t REG_SZ /f
C:\Windows\sysnative\reg.exe add HKEY_CLASSES_ROOT\thinkorswim\shell\open\command /ve /t REG_SZ /d "\"C:\Program Files (x86)\thinkorswim\thinkorswim.exe\" AutologinLink %1" /f
C:\Windows\SysWOW64\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Version Vector" /v tossc /t REG_SZ /d 1.0 /f
C:\Windows\SysWOW64\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Version Vector" /v thinkorswim /t REG_SZ /d 1.0 /f
C:\Windows\sysnative\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Version Vector" /v tossc /t REG_SZ /d 1.0 /f
C:\Windows\sysnative\reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Version Vector" /v thinkorswim /t REG_SZ /d 1.0 /f
You can then launch ToS with any of these:
# To launch from anywhere (if you alread have java installed or in ToS directory.)
javaw.exe -cp "C:\Program Files (x86)\thinkorswim\suit\1968.2.0\tos-suit-1968.2.0.jar" com.devexperts.jnlp.platform.impl.windows.WindowsSharedConfigurationLauncher SharedConfigurationLink A1PZUml
# To launch from ToS directory
.\thinkorswim.exe AutologinLink A1PZUml
.\thinkorswim.exe SharedConfigurationLink tossc:A1PZUml
Unfortunately none of these give any further info on how to get or see the thinkscript.