Set up:
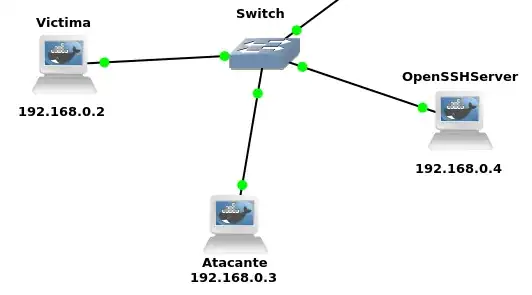
- Victim:
192.168.0.2 - Attacker (also having SSH server installed):
192.168.0.3 - SSH server:
192.168.0.4
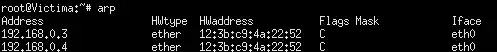
I perform a successful ARP Spoofing attack (being obviously the attacker's MAC address):
But when I try to connect via ssh user@192.168.0.4, instead of connecting to the attacker's ssh server, it redirects the traffic to the real ssh server (or keeps waiting for this connection if traffic redirect is disabled in attackers /proc/sys/net/ipv4/ip_forward file).
Is there any way I could interpret packets coming from an IP before redirecting to the original destination?
Note: in case it's relevant, I'm using Ubuntu docker containers inside GNS3 inside a VM. This is the scheme: