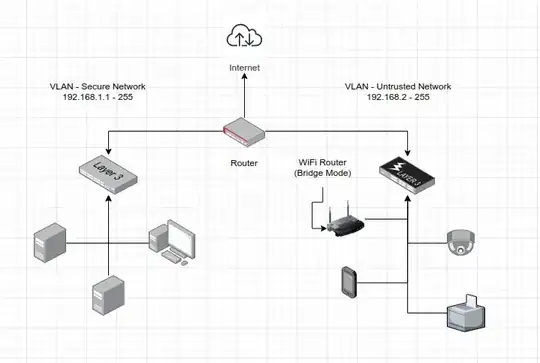
To keep attacks out of a secure network, limit the ways they could break-in. For example, don't put a WiFi router on the secure network because anyone can connect to it even from outside your house. Also if the devices on either network don't need to talk to each other, create a firewall that restricts that traffic.
If you're creating VLANs on the router, make sure that you can't access the admin interface over WiFi. Anyone can just hack your wifi signal and login to the admin interface, and undo all of the security, and jump between VLANs. Look into VLAN hopping if you're creating VLANs on the same switch.
https://en.wikipedia.org/wiki/VLAN_hopping
All smartphones should be put on an untrusted network because any device that you walk around with every day in unknown environments can never be trusted. If you need to access something on the secure network from your phone, create a firewall rule if your router supports it.
I would recommend installing a dedicated router like pfSense or OPNSense on an old PC and use that as a router instead of a WiFi/router combo. Then put your WiFi router in bridge mode (which means it gives out IPs from pfSense and assigns them to the devices on WiFi).
IP cameras should also go on the untrusted network and shouldn't have internet access or access to any other device on your network. A firewall rule should take care of that easily.
https://www.forbes.com/sites/zakdoffman/2019/08/03/update-now-warning-as-eavesdropping-risk-hits-millions-of-chinese-made-cameras/?sh=1930561d6bf2
Make sure your router is secure by ensuring your Wifi network has a strong password. And installing the latest firmware (should be on the manufactures website). Don't buy routers from companies you've never heard of, however, even routers from reputable companies can also be plagued with security vulnerabilities.
https://www.fortinet.com/blog/threat-research/fortiguard-labs-discovers-vulnerability-in-asus-router
https://nakedsecurity.sophos.com/2020/07/24/asus-routers-could-be-reflashed-with-malware-patch-now/
To regulate who has access to the network, most routers have a feature where you have the router only give out IP addresses to devices that you have whitelisted. That way if someone were to plug in an untrusted device, it wouldn't get an IP and couldn't connect to the internet.
https://helpdeskgeek.com/networking/how-to-whitelist-specific-devices-on-your-home-network-to-stop-hackers/
https://docs.netgate.com/pfsense/en/latest/services/dhcp/ipv4.html#mac-address-control
Here's a diagram of what I was talking about above.