I stumbled on a Windows bug leading to code execution. I believe it should be categorized as a vulnerability but Microsoft does not recognize it as such. I would like to read other opinions.
Functionality
The bug affects the context menu "Open PowerShell here" which is activated when a user SHIFT-right clicks on a folder in Windows Explorer.
Normal behaviour
Normally that command is supposed to open a PowerShell terminal with the working directory set on the specified folder.
The Bug (Vulnerability?)
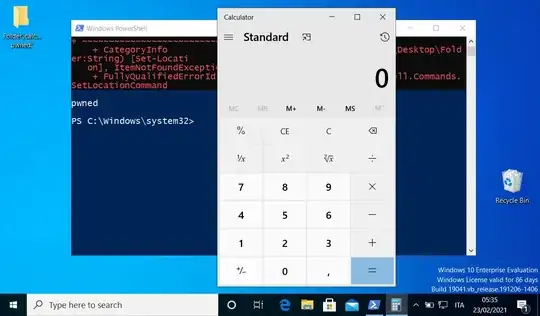
The bug is triggered when a folder contains a single quote (apostrophe). In that case the PowerShell terminal executes what follows the apostrophe as if it were a series of PowerShell commands.
For example when opened in this manner, a folder name of Folder Name';calc;echo pwned;' would open the calculator and write pwned on the terminal, as follows:
Possible Implications
This bug could be abused leading to unauthorized code execution in those contexts where victims are likely to use PowerShell on folders names crafted by attackers (USB keys, ZIP files, network shares). It requires user interaction which for certain classes of users is part of the normal daily workflow. It is not easily discovered as malicious folder names can be hidden by preceding them with long strings and following them by clearing the console.
What I did so far
I submitted the bug to the Microsoft Security Response Center, who replied that it "does not meet the definition of a security vulnerability". The CVE-ID submission form instructs to contact Microsoft directly. Sans and the my national CERT did not reply.
Questions
- Would you consider this as a security vulnerability?
- If so, how would you classify it? (injection, local/remote code execution etc.)
- Should it be covered by the Microsoft Bug Bounty program?
- How would you report it given the reactions?