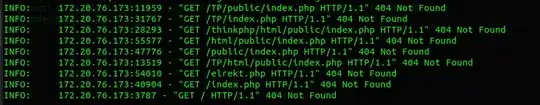
I'm running a docker container in Kubernetes cluster running in aws, I exposed the container through LoadBalancer service and limited access to it just to my ip address using aws security groups, but I still getting GET/POST requests that seems brute forcing the endpoints of the application.
My question is how is this possible even I limited access just to my ip address? and how I could mitigate this issue?