I'll formulate my question in regards to timestamped PDF, but I wonder actually about the long term validation of RFC3161 tokens in general.
So, PAdES has the concept of Long Term Validation, which means (correct me if I'm wrong), that a document contains all the necessary data to confirm even after a certificate has expired or has been revoked whether the signature was valid at the time of signing. For this the document must contain for each certificate in the trust-chain up to the trust anchor either OSCP replies or CRLs (depending on what each certificate specifies to use for revocation checks) that show validity of the certificate at the time of signing.
Now, using RFC3161 it's possible to timestamp documents using a trusted TSA so one can prove that a document has existed at a certain point in time and has not been altered ever since. With PDF 2.0 it's also possible to embedd such timestamps without signing the document additionally (called Document timestamp).
In Adobe Reader, such a timestamp will show like this:
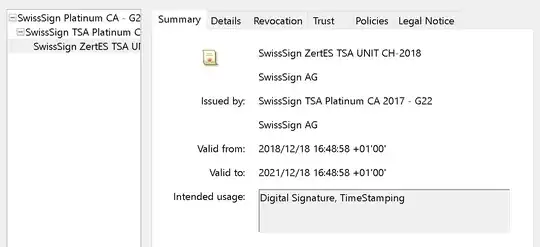
A timestamp token contains the hash that was requested to sign, the date (as determined by the TSA) plus some other metadata, which is then signed by the TSA certificate. The trust-chain in this case looks like that:
So, the timestamp token was signed by "SwissSign ZertES TSA Unit CH-2018".
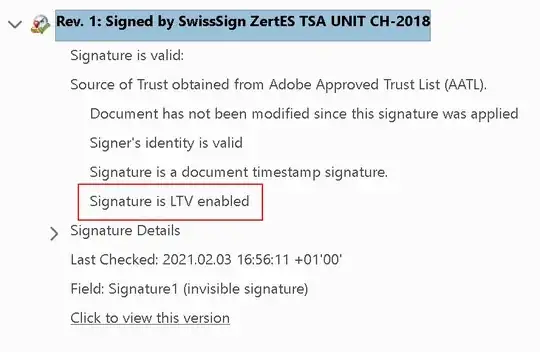
Now, by embedding CRLs and OSCP replies for this certificate and its trustchain, I can "LTV enable" this timestamp, which would mean that it would remain valid also beyond the valdity of the signing certificate. If I do so, Adobe Reader will show the timestamp as LTV enabled:
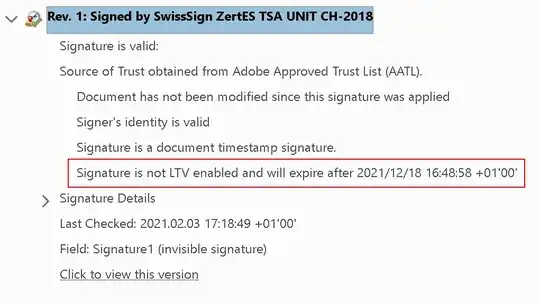
What I wonder though is what that Long Term Validity actually means for timestamps? If the Private key of "SwissSign ZertES TSA Unit CH-2018" would leak (and subsequently the certificate would get revoked), wouldn't that render any timestamps signed by it invalid anyway? someone in possession of that leaked key could change the document and create back-dated timestamp tokens using that certificate, couldn't he? So how exactly can a trusted timestamp have 'long term validity'?
And as an additional question: If the private key of a RFC3161 TSA does leak, is there any possible contingency procedure to restore the validity of already issued tokens (using the signing log of the TSA server for example)?