I have a Windows 10 computer with 3 hard drives:
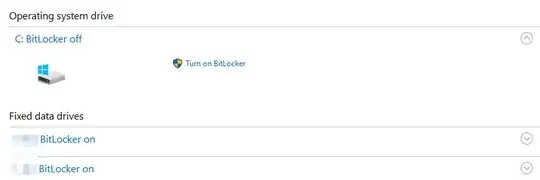
- Samsung SSD 850 EVO 1TB (SSD, system drive where Windows 10 is installed, not encrypted yet)
- First 3 TB HDD already protected by BitLocker
- Second 3 TB HDD already protected by BitLocker
Whenever I boot into Windows, I need to type in long passwords to unlock the second and third drives. It's annoying.
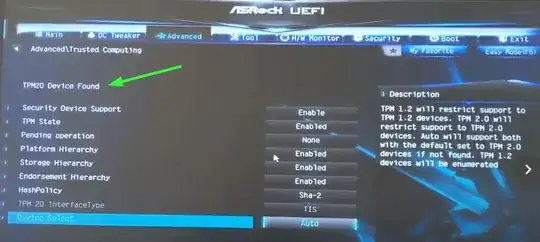
So I was excited to finally install this ASRock TPM2-S TPM Nuvoton NPCT650 Trusted Platform Module onto my Z170 Pro4 motherboard (which is running firmware 7.50) today because my understanding was that I would then be able use BitLocker on my system drive too and won't need to keep entering long passwords for each other drive on each boot into Windows.
I do not want to use a USB key. I just want my main Windows password to automatically decrypt all 3 drives when I log into Windows.
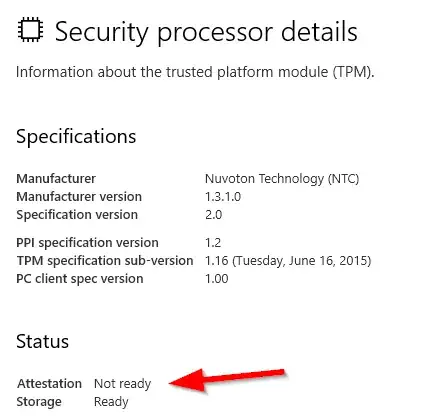
The BIOS successfully recognized the installation of the TPM:
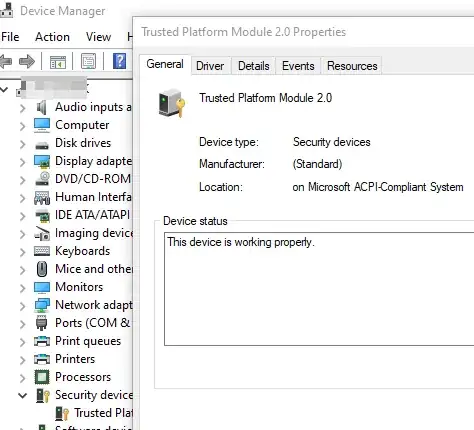
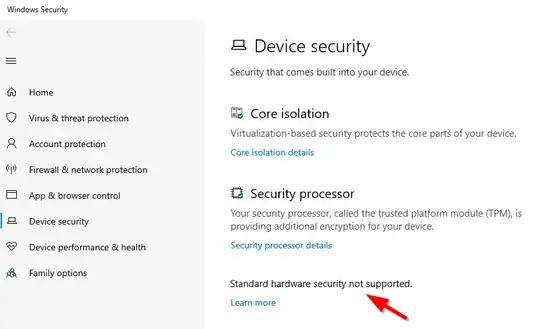
And Windows 10 did too:
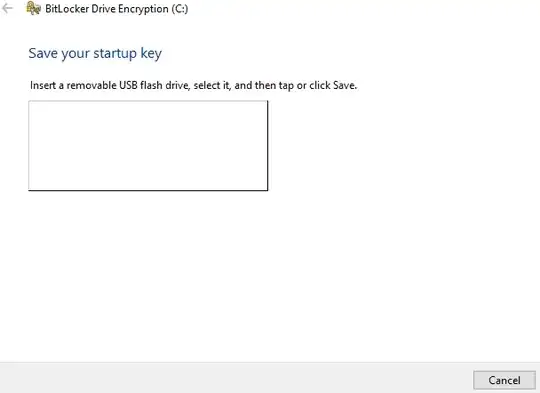
Here is my problem. When I click "Turn on BitLocker" for my C drive, it forces me to set up a USB key, which I don't want to do:
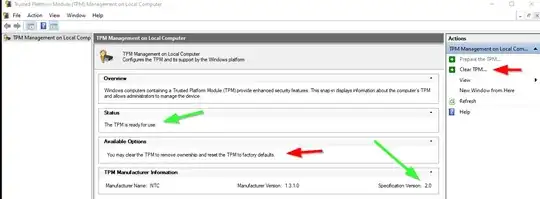
I have already tried clearing the TPM:
I also tried changing settings in Windows Local Group Policy Editor, but then when I clicked "Turn on BitLocker" for my C drive, I got the error: "The Group Policy settings for BitLocker startup options are in conflict and cannot be applied. Contact your system administrator for more information." (With other settings, I got: “The startup options on this PC are configured incorrectly. Contact your system administrator for more information.”)
What am I doing wrong? How can I enable BitLocker on my C drive without setting up a USB key?