I've noticed a lot of phones (not to mention, other devices) have built in fingerprint sensors these days.
Do these devices store information in such a way that your fingerprint could be reconstructed by someone with access to it?
I've noticed a lot of phones (not to mention, other devices) have built in fingerprint sensors these days.
Do these devices store information in such a way that your fingerprint could be reconstructed by someone with access to it?
Devices that support biometric authentication are equipped with Trusted Execution Environment (TEE) that stores fingerprint data in its own isolated tamper-resistant storage. The biometric sensor communicates with sensor driver which lives inside TEE. When a user wants to enroll fingerprint, fingerprint data from the sensor goes directly to the sensor driver where it is stored by TEE.
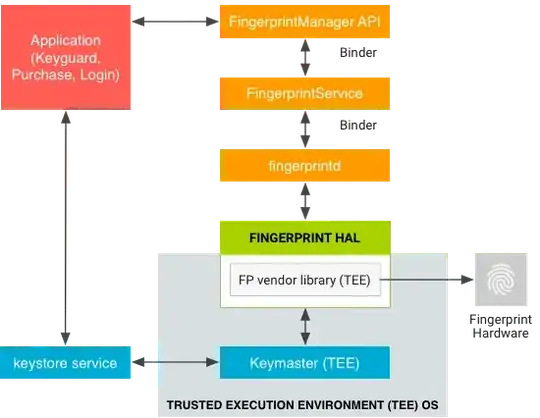
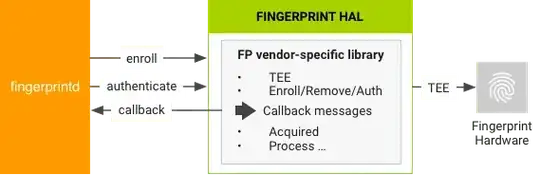
At the time of biometric authentication, TEE only answers whether the fingerprint was correct or incorrect. Raw fingerprint data is never accessible from outside the sensor driver. Hardware access is limited to the TEE and protected by an SELinux policy. The Serial Peripheral Interface (SPI) channel is accessible only to the TEE.
TEE does not hash fingerprint data because every time you put your finger differently on the sensor. The mathematical values can be used to reconstruct your fingerprint if algorithm is known.TEE encrypts fingerprint data with a symmetric key. It also signs biometric metadata that is outside of TEE and is used by TEE in validating fingerprint. So if you try to swap TEE chip with your own device's TEE, signature check will fail along with user authentication.
Even if you obtain root access on the device, fingerprints that are already stored in TEE can never be extracted. Patching sensor driver to leak fingerprint data will fail signature check of TEE image on boot and the device will brick. TEE image is still verified even if the bootloader is in unlocked and unlocked_crirical state. Emulating TEE on rooted device is still not enough to hijack sensor communication as SPI channel is bound to the real TEE.
Theoretically, you can compromise SPI channel with hardware debuggers on unrooted device to leak future accesses to the sensor but this attack is not scalable. In order to test sensor driver, some OEMs intentionally leak sensor data to testing application in prototype devices. It seems Mi forgot to disable the access for some of its production devices which is a security hole because any application can access sensor data on those devices. How this is not already violating SELinux policy is unclear.
The easiest way to reconstruct fingerprint is to copy prints from the surface. Fingerprint protection is as secure as physical protection.
The best analogy for this is that most biometric templates stored on devices are like hashes of a password. You don't ever persist the password itself and instead persist the hash of it. You never store the raw fingerprint data itself and instead store the template, which is a derived value of the raw data.
However, like hashes there are varying degrees of hardness to reverse. With relatively little effort I can reverse md5(yourpassword), but it is practically impossible to reverse pbkdf2(yourpassword) (contrived example, there's more to it than that).
There isn't a lot of research on this for fingerprint/biometric data like there is for cryptographic hashes and a lot of these algorithms in devices are still proprietary so its difficult to offer a more specific answer.
The question though is supposing you were able to reconstruct the fingerprint, what would your intentions be with it? Many of these sensors have methods of detecting replays through liveness detection (and other mechanisms) so constructing a fake print would be incredibly difficult. Using it for non-repudiation is a bit redundant since you only need the template for that anyway.