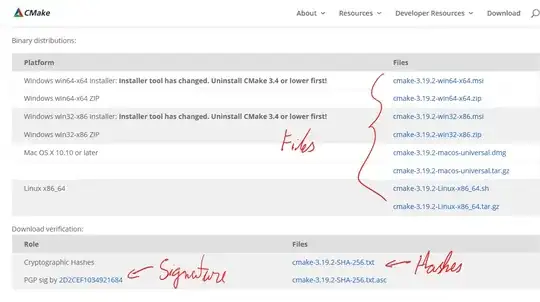
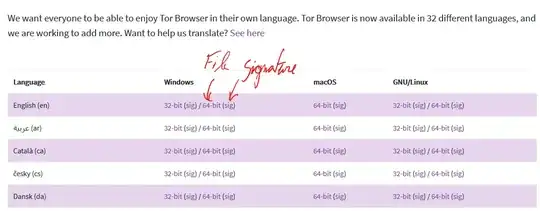
When downloading files (mainly software/installers) from pages in browsers, sometimes it comes also with a cryptographic hash or a signature to verify the authenticity of a file against data manipulation (example below).
Why there isn't something that automatically says to the browser "Hey, this is the link to download the file and this is the link to download the signature, download both and check its authenticity"?
Is there a vulnerability issue?
And if there exists some extension or something else that does this, please tell me.
It would be really nice to have something that automatically checks the integrity and authenticity of downloaded files.