I'm currently learning about network security and came across a problem, maybe I'm just missing something obvious but I'll try to explain my environment:
I have a Kali Linux VM connected to the WAN Interface (192.168.178.109) of a Pfsense VM, the PFsense has another LAN (.2.1) and DMZ (.1.1) interfaces with a few VMs connected to each Interface. On the WAN Interface, I disabled all incoming traffic except some NAT rules for port forwarding to hosts in the DMZ (i hope i explained that correctly).
Now, if i run nmap -sV –open –reason PFSENSE_WAN_INTERFACE on my Kali VM it successfully scans the forwarded ports and shows the services in the DMZ:
| PORT | STATE | SERVICE | REASON | VERSION |
|---|---|---|---|---|
| 21/tcp | Open | ftp | Syn-ack ttl 127 | Microsoft ftpd |
| 25/tcp | Open | Smtp | Syn-ack ttl 63 | Postfix smtpd |
| 53/tcp | Open | Domain | Syn-ack ttl 64 | (generic Dns response: REFUSED) |
| 80/tcp | Open | http | Syn-ack ttl 63 | Apache httpd 2.4.46 ((Ubuntu)) |
| 444/tcp | open | https | Syn-ack ttl 64 | Nginx (Pfsense) |
But if i try to do a vulnerability scan with GVM, it doesn't find anything. When I enable the allow any rule on the WAN Interface, the scan shows results, but i don't want to have the interface open. Are there some settings in GVM I am missing? Am I doing it completely wrong?
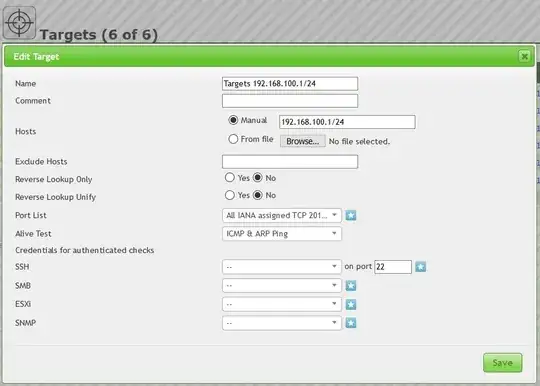
Here is a Screenshot of the firewall settings of the WAN interface:

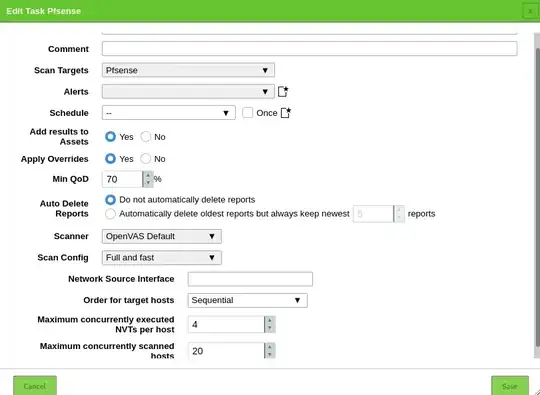
Here is a Screenshot of the GVM task:
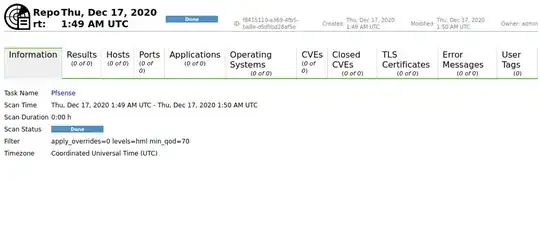
Here is a Screenshot of the GVM task report:
Some advice would be gladly appreciated, and if neccessary, i can provide more information.