I'd like to build an IPS which would be a seperate endpoint than the router and/or protected servers. To achieve this I've installed to my Ubuntu server Snort with DAQ(AFPACKET). The instructions I've used is here -> Snort 3.0.1 on Ubuntu 18 & 20
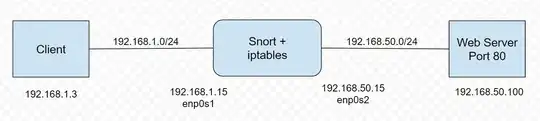
I've built a local network which to simulate a real use case. For simplicity I'd like to focus on IPS protection and simple routing. The network I'm trying is below:
Now that I can perfectly configure the iptables to forward the outside(192.168.1.0/24) network to inside network (192.168.50.0/24) with such commands:
sudo iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT --to-destination 192.168.50.100:80
sudo iptables -t nat -A POSTROUTING -o enp0s1 -j MASQUERADE
Seperately, I can redirect the outside(192.168.1.0/24) network to Snort's NFQUEUE
sudo iptables -I FORWARD -j NFQUEUE --queue-num=4
sudo snort -c /usr/local/etc/snort/snort.lua -L dump --daq afpacket --daq-var queue=4 -i enp0s1:enp0s2
Unfortunately I'm having a hard time to understand to combine these both commands to use Snort as complete IPS tool. So in short how I can make Snort to forward inspected 'secure' client packet to the webserver then back(of course).
Much appreciated