In my opinion you're not overthinking it. Rightful access during an emergency is as much part of the information security puzzle as other considerations. I'm in a similar situation and part of our solution involves the use of KeepassXC with a second factor, which is already mentioned by others, but for which I will expand on in this answer. KPXC can be used on numerous platforms. I also draw to your attention two additional utilities that make this a good choice:
- KeepassDX, which gives you access to your kdbx file on an Android device ^1,
- and keepassxc-cli, which grants automated exports from the command-line.
Exporting the contents of a kdbx from the cmdline
Firstly, you don't actually need to automate the export. You can periodically produce a plain-text export from the secrets database using the Database > Export > CSV menu option, and place this file somewhere secure. You could theoretically place this into an encrypted container, eg LUKS or Veracrypt. Of course, unlocking, mounting, writing to, and un-mounting such a container could also be automated using a similar auto-type technique, described subsequently.
To export the kdbx entries in semi-structured form (xml) from the command line, using keepassxc-cli:
keepassxc.cli export --key-file ~/Desktop/.N.key ~/N.kdbx
Now, in our case, the export is piped to openssl, which in turn encrypts using a complex password that likely can't be remembered, but can be transcribed relatively easily ^3 on a phone's soft-keyboard.
#!/bin/bash
_KFILE="Nkdbx.$(date +%Y%m%j%H)" &&
_KPXRT=$(keepassxc.cli export --key-file ~/Desktop/.N.key ~/N.kdbx) &&
echo -n "$_KPXRT" |
openssl enc -aes-256-cbc -pbkdf2 -iter 3000000 -out "$_KFILE" &&
unset _KPXRT && chmod 0400 "$_KFILE"
To decrypt the export backup in the future, but limit the output on the cli using grep (ie. once you decrypt and print to the cli, you must then change those account passwords to ensure the credentials can't be found in some scroll-back buffer or log):
openssl enc -d -aes-256-cbc -pbkdf2 -iter 3000000 -in Nkdbx.2020xxx | grep -9 'ACCOUNT_CLUE'
... where ACCOUNT_CLUE is some search string for the account details you're looking for
Configuring a new KPXC entry to auto-type an encrypted export
In KPXC, you can create entries that are configured to auto-type into a terminal window, which unlocks a particular KDBX file, and dumps the content into a plain-text file using keepassxc-cli ^2.
The use of these auto-type entries is done by bringing up a terminal window, then switching back to your KPXC window, then selecting the appropriate entry, right-clicking, and selecting Perform Auto-Type. KPXC will now switch back to the terminal window and execute the command on your behalf.
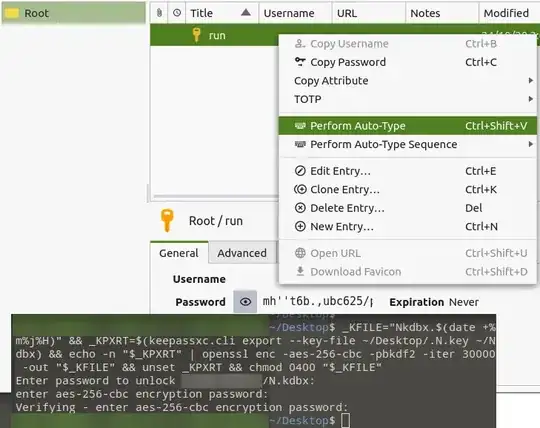
You configure auto-type through the Auto-Type settings in password Edit entry, and you manage the commands in the Edit entry > Advanced > Additional attributes section.
First, we'll add an attribute called CLI_PWD and tick PROTECT. Now, click Reveal and then click in the edit box. Finally, type the password for this kdbx into this, then Apply.
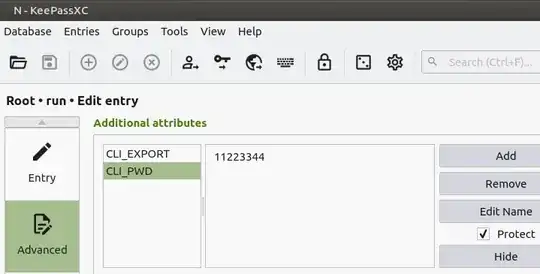
We'll add an attribute called CLI_EXPORT with the value described previously, but now on a single line:
_KFILE="Nkdbx.$(date +%Y%m%j%H)" && _KPXRT=$(keepassxc.cli export --key-file ~/Desktop/.N.key ~/N.kdbx) && echo -n "$_KPXRT" | openssl enc -aes-256-cbc -pbkdf2 -iter 3000000 -out "$_KFILE" && unset _KPXRT && chmod 0400 "$_KFILE"
Next switch to the Auto-Type section for the entry and choose use custom auto-type sequence:
{S:CLI_EXPORT}{ENTER}{DELAY 400}{S:CLI_PWD}{ENTER}{DELAY 4000}{PASSWORD}{ENTER}{DELAY 250}{PASSWORD}{ENTER}
This bit can be tricky, and will depend on your machine as well as the parameters you chose for your kdbx security ^1. On my machine, {DELAY 400} is enough time for keepassxc-cli to load and parse the kdbx file, and {DELAY 4000} is enough time for the kdbx file to be unlocked. What will happen if these auto-types occur too early is that the secrets will show up in the command line - everything else works as expected, however, because it is still read as stdin.
Doco is here: https://keepassxc.org/docs/KeePassXC_UserGuide.html#_configure_auto_type_sequences
I should note that this is a manually triggered process that results in a separate exported file that doesn't rely on KeepassXC, rather, only openssl. We still bak the kdbx file through a separate automated process.
The choice of openssl to secure the export is debatable, because it doesn't provide for integrity of the encrypted file at this time. I vaguely remember reading somewhere that it wasn't possible to modify openssl to use AEAD on the command line, because the output format couldn't be modified to include the authentication tag, and still maintain backwards compatibility. If this is important to you (ie. if your encrypted export is readily accessible by potential adversaries), then another tool such as age, see https://github.com/FiloSottile/age could be a better choice.
Notes
^1
Some sensible, long-term settings for your database security would be:
- use a password and a keyfile
- use KDBX version 4, KDF Argon2 - Argon2 is a password-based key derivation function (PBKDF) that has tunable 'hardness factors', designed to slow down the dictionary-based attacks to determine the password that generates your master encryption key
- if you intend using this on Android devices with ARM:
- if you'll only ever access using a desktop/ server, with AES cooked into the cpu core:
- AES or ChaCha20
- RAM 1024MB
- parallelism 8
- rounds 15
- set yourself a task to review these numbers each year - you can change them after the fact, as processors get more powerful
^2
This works in KPXC, but to be sure I would un-select 'automatically save after every change' in the settings, so the kdbx file doesn't get modified when you perform 'auto-type' - this may not suit your needs, the downside being that your changes aren't automatically saved: you now need to manually save the database, or wait 'til it locks. I've looked through the source code a while ago and couldn't see anything that may lead to corruption, however, to be sure you should also un-select automatically reload the database when modified externally and select safely save database files.
^3
A starting choice would be 14 lower-case alpha and numeric characters, chosen at random and each possibility being equally likely, which you then extend by distributing five additional punctuation characters throughout the password, chosen from the range that can be typed on a soft-keyboard on a phone without the use of the SHIFT-modifier. I calculate the strength for this to be over 80 bits of CS-entropy, ie. log-base2 (36^14 x 5^5).
You must, of course, write this down somewhere once the password manager picks it. To decrypt on any Android phone, you can instal Termux and then add the openssl utility pkg search openssl and pkg install openssl-tool
Argon2
Argon2 inputs and outputs - https://tools.ietf.org/id/draft-irtf-cfrg-argon2-05.html#rfc.section.3
Message string P, which is a password for password hashing applications. MUST have length from 0 to 2^(32) - 1 bytes.
Nonce S, which is a salt for password hashing applications. MUST have length not greater than 2^(32)-1 bytes. 16 bytes is RECOMMENDED for password hashing. Salt SHOULD be unique for each password.
Degree of parallelism p determines how many independent (but synchronizing) computational chains (lanes) can be run. It MUST be an integer value from 1 to 2^(24)-1.
Tag length T MUST be an integer number of bytes from 4 to 2^(32)-1.
Memory size m MUST be an integer number of kibibytes from 8*p to 2^(32)-1. The actual number of blocks is m', which is m rounded down to the nearest multiple of 4*p.
Number of iterations t (used to tune the running time independently of the memory size) MUST be an integer number from 1 to 2^(32)-1.

