I have three domains but the same code base (Domain X, Domain Y, Domain Z) and Accounts website A
If a user tries to sign in accounts from domain X, I wanted to SSO in the other two domains (Browser Scenario: third party cookies blocked).
I tried the following approach,
- Go to Accounts from Domain X
- Sign In
- Get the required authentication token info and posts an XHR request to Domain Y to create a cookie.
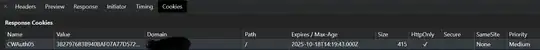
When I check the request in Network, the required cookie is set in the response cookies, but when I open Domain Y separately the cookie is not present in the Application Cookies.
Can anyone please tell why the created cookie via XHR request is not accessible by the main domain? Kindly help.
XHR request (withCredentials set to true):
$.ajax({
type: "POST",
data: result,
url: result.uri,
beforeSend: function (xhr) {
xhr.withCredentials = true;
},
success: function (data) {
console.log(data);
}
});
Cookie Info:
HttpOnly: true Secure: false SameSite: None