That article mentions a new "security warning" in which:
On the web or Android, if you receive a message that can’t be authenticated with either Sender Policy Framework (SPF) or DKIM, you’ll see a question mark in place of the sender’s profile photo, corporate logo, or avatar.
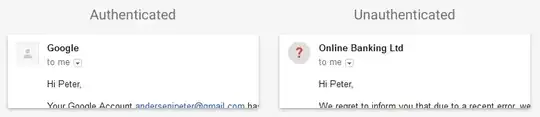
This has nothing to do with accepting a message for delivery. All it means is that, when neither DKIM nor SPF pass (presumably with alignment), the image used to represent the sender will be replaced by that gray stop-sign with a bold red question mark on it, as demonstrated in the screen shot.
This was an early attempt at something like BIMI (though in the other direction; this is an image to warn of potential spoofing rather than an image that is robust against spoofing) and I think it's a good protective step.
As of 2016, Google and many others block mail when DMARC invokes its reject policy, so this only affects senders that do not use DMARC p=reject (which can only trigger when neither SPF nor DKIM passes with alignment).
Back before DMARC, SPF was widely deployed and its use of -all and ~all had very low efficacy; blocking based on either would result in blocking vast volumes of legitimate mail. The SpamAssassin community even concluded that ~all (soft fail) was a stronger spam indicator than -all (hard fail)!
Without DMARC, senders don't see when their mail fails to properly verify with DKIM or SPF (barring RFC 6652, which I've never seen used). They therefore cannot determine if their failure condition (spf -all) works (and DKIM doesn't a failure condition) and neither has a suggested failure policy. DMARC provides the reporting mechanism to determine what issues may arise with a blocking policy and then lets senders issue such a policy.
If you want to require DKIM, I suggest an SPF record of v=spf1 ?all so that SPF can never pass (nor can it ever fail). Then your DMARC p=reject can deny any mail purportedly from your domain unless it passes DKIM. At that point, SPF isn't necessary (DKIM is really hard to replay and basically impossible to forge).
