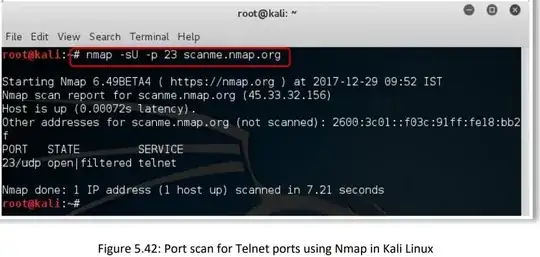
I am pushing my way through some beginner level security readings and exercises (ECSA 1 & 2) without much of a networking background. I happened upon an interesting suggestion or command: to use nmap -sU -p 23 target to find out if a target is running a telnet service. I hopped over to the telnet Wikipedia page and found that telnet is a TCP based protocol (it likely doesn't use UDP). Even RFC 854 states that "A TELNET connection is a Transmission Control Protocol (TCP) connection".
I've not dove very deep into the related protocol specifications (and perhaps I should), but I've caught myself in my own confusion or mistaken assumption. How does nmap -sU (a UDP scan) detect if a TCP port is open or closed? Are there ever reasons to match the target port/service protocol or is detecting the state of a port somehow completely independent of the target port (and its bindings?)? How so?
If your answer(s) is to simply point me to some reference material that's fine. I realize I might be trying to take some shortcuts here.
Update:
The book gives a little background about the telnet service but does not specify whether or not it is TCP or UDP based. It then says "You must scan the telnet ports using Nmap with the following command: nmap -sU -p 23 x.x.x.x". I can't quite tell if that's bad advice or not? Informative either way I think.