I am new to Kali Linux and JTR but am playing around trying to crack a PDF file. I set the PDF Password to test so it's a known password on my own file. For whatever reason JTR appears to finish cracking the file but returns (?)
What am I doing wrong, is JTR only able to crack document view passwords not document edit passwords for PDFs?
This is my file hash from running pdf2john:
root@kali:/usr/share/john# cat ~/Desktop/newcrack.hash
$pdf$5*6*256*-1052*1*16*2bd413a2a376d44b8bf88bd6946d0fe6*127*6539386315f0a6efb9af1af2ec0ddc97286e63f6e8f0f90cc55cd728d58e7c2b038470eb183135c033035d9f00c20bbd00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000*127*17a60bd7d6d2598f18d49e8b79d39b4a01fdab4e0f8a39a5638d751a969537537d34a956b5a58d112cc1332b9e84f81600000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000*32*6d1958871a16b03631acbd5d7d252c84d7c144a120dee6ce4d234553c1602b04*32*53e87e7cf2aeb4799558586ef310e26c1af5640ce9ad4d4d676f2307958c5dd6
I then run john on the hash using the crackstation.txt file which is a 16GB flat file wordlist:
root@kali:/usr/share/john# john --wordlist=/root/Desktop/crackstation.txt ~/Desktop/newcrack.hash
Using default input encoding: UTF-8
Loaded 1 password hash (PDF [MD5 SHA2 RC4/AES 32/64])
Cost 1 (revision) is 6 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
(?)
1g 0:00:00:00 DONE (2020-08-30 00:20) 5.882g/s 376.4p/s 376.4c/s 376.4C/s ..```.....
Use the "--show --format=PDF" options to display all of the cracked passwords reliably
Session completed
When showing the password it looks like it's blank but I set it to test so it should be able to crack it.
root@kali:/usr/share/john# john --show ~/Desktop/newcrack.hash
?:
1 password hash cracked, 0 left
It seems like JTR is assuming the password is blank, returns immediately, and reports the password hash was cracked however the show command does not show any password.
Can anyone tell me what I am doing wrong here?
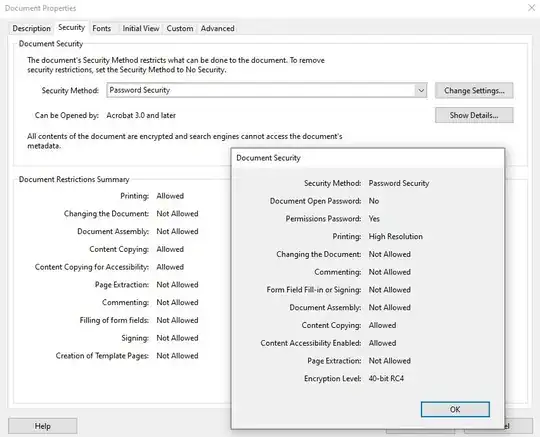
Update: I ran a few tests and figured out that John The Ripper does not appear to remove PDF "Permissions Protected" passwords. I password protected the same document two different ways then ran JTR on the hash. First I password protected for "Document Open" using the test password. I entered that into JTR and it worked! It cracked it no problem. I then removed the "Document Open" password and added a Permissions Password of test. JTR will NOT crack that, it simply returns NULL every time. So my only conclusion is that JTR does not work on Permissions Passwords. Someone please correct me if I'm wrong. I could not find any documentation on this.