I recently came across an application that was vulnerable to HTML injection on the invite function. When I insert <img src="image.jpg"> the image got rendered on the mail I received.
I decided to test for blind ssrf out of band detection, so I gave the payload as <img src=" burp collaborator payload"> and sent the invite. When I analyzed the Burp collaborator I received a DNS Query which was like this below.
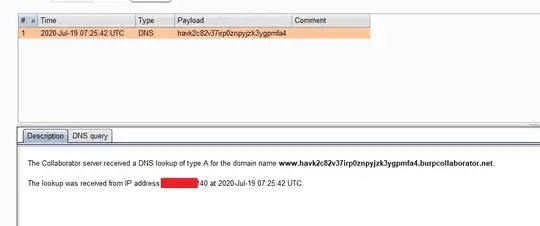
I couldn't get any HTTP request from the server.
Is this vulnerable or not? If not, is there any possible way to escalate or any bypassing methods to get the HTTP request?