https://exchange.xforce.ibmcloud.com/vulnerabilities/31739
linuxpam-pamunix-security-bypass (31739) reported Jan 23, 2007
Linux-PAM could allow a remote attacker to bypass security restrictions, caused by a vulnerability in pam_unix.so when handling password hashes that consist of two characters. An attacker could exploit this vulnerability to bypass security restrictions and gain unauthorized access to the system using arbitrary accounts.
Consequences: Gain Access
Can someone please explain to me how to actually implement this exploit?
I am currently working on HTB cache and I've gained RCE to EMR application. I've
gained access to /var/lib/pam which shows the following:
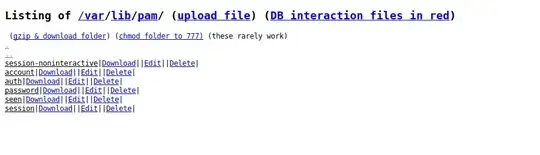
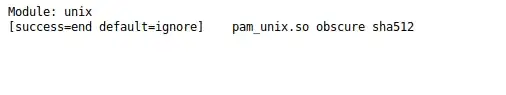
Will these be of any use to me? I'm trying to gain root/user access.