I have installed a Windows machine with update 1909 (build 18363.720 (March 2020) (On which I try to find vulnerabilities with nmap), which includes smb 3.1.1 with the latest fixed bugs. I created a shared folder on this machine and made the various configurations on the firewall so that the shared folder can be accessed from the outside (private, public and domain firewall enabled and let connections access the share if the password is given). Of course with a password complex enough not to be cracked easily.
I then opened the smb port 445 (for smb 3) on my router, which I redirect to the local ip of this machine only.
(I also created a dyndns so that the ip updates of my router are updated automatically.)
So I can access my share from anywhere.
I can already see people coming from afar saying that it's very dangerous to open ports directly on the internet, and they will be right (VPN is better, obviously). But I wouldn't like to have to have a debate about VPN.
"Is it secure enough for a small home system" to reasonably imagine sharing files, media and vacation pictures with colleagues (by being explaining to them that they just have to create a network shortcut on the network path of my dyndns), without having to worry about getting hacked in 3 minutes? Of course I will patch my system each time I find it necessary (2 or 3 times a year). It's also an easier way to set up file-sharing without having to install third-party tools like with NAS Synology etc.
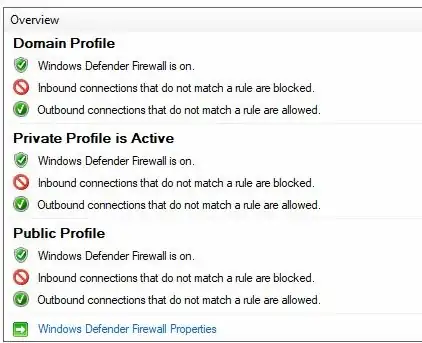
Here are my target machine firewall configs associated to port 445
and here we see that domain, public and private are active
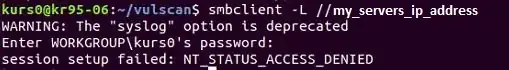
and this is what is displayed when someone tries to connect to my share from the internet (with ubuntu) with a wrong password
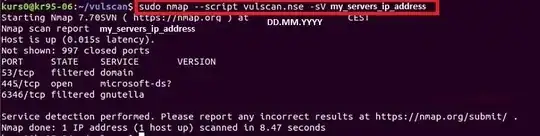
I did some tests with nmap in order to find possible flaws in the port I opened. Here are the results with vulscan and nmap-vulner.
Here Nmap-Vulner
Are there other tools which i can test to check the security of the smb server?
Would it be reasonable to buy extra hardware in order to enhance security?
Otherwise, should I just shut down my smb port and install a VPN with a NAS Synology or other hardware?