Last week, I downloaded Kali Linux from the official https://www.kali.org/ website for educational purpose. I left the downloaded disc image (.iso) on my desktop. Yesterday, Windows Defender decided to run a quick scan and went through the Kali Linux .iso file. We know that anti-virus softwares usually do not like such hacking tools and consider them as threats.
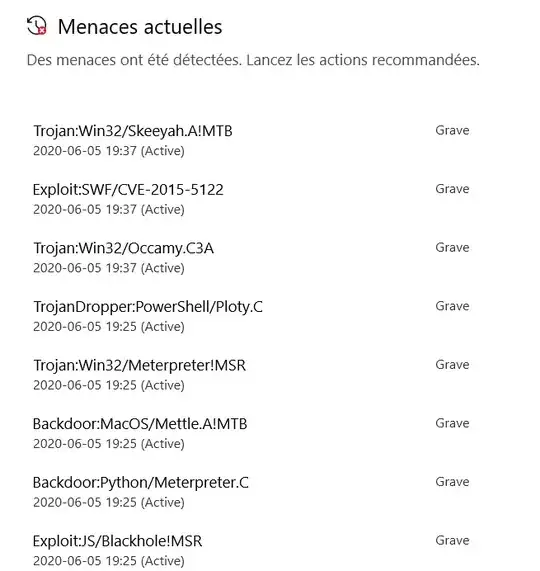
So, Windows Defender reported 329 threats found (mostly Metasploit payloads), certainly all from the Kali Linux image.
I click the start recommended action button, but it seems to be stuck at the spinning wheel "removing threats".
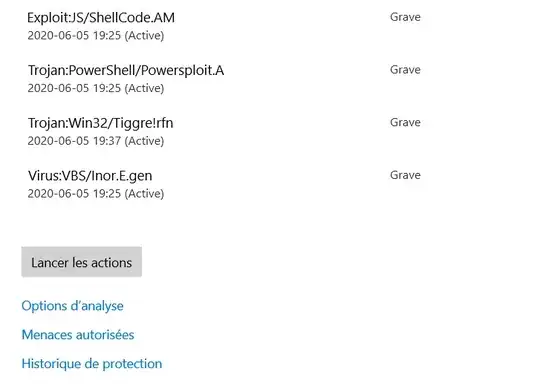
Here is a sample of threats that were found in the .iso file.
The button "run actions" does not clear the history. If I deleted the .iso file, running another scan won't report any threats, but the history of the previous scan is still there.
I'm a bit worried that Windows Defender could have executed the malicious code contained on the Kali Linux .iso file on my computer because I clicked on the "run recommended actions" button without knowing exactly how it gets rid of the threats found in the disc image. Actually, the threats found could not even be deleted, is it because they are in a disc image and Windows Defender can't delete them inside the image ? Does it "copied" the malicious code on my computer ?
Now, Windows Defender always report 329 threats found, even if I deleted the Kali Linux image. How I can securely and in a clean way, clear the Windows Defender history ?
Should I consider wiping my all my hard disks and reinstall Windows to be sure there's any malicious code installed on my computer from this disc image ?
I currently found a way to clear up Windows Defender history, it consists of deleting this folder : C:\ProgramData\Microsoft\Windows Defender\Scans\History\Service
Thought, I'm not sure if it is a clean way to do that. What do you think about ?
Configuration: Windows 10 x64, build 1903