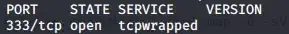
I'm doing a nmap scan to my own machine to my own machine. First of all I set the port 333 to listen with this command sudo nc -lvnp 333
On the other terminal I run sudo nmap -O -sV -p 0-65535 IP where IP is my local IP. The result I got on the nmap terminal is this one:
But on the terminal where I opened the port, the process finishes and I have this message:
root@kali:~$ sudo nc -lvnp 333
listening on [any] 333 ...
connect to [IP] from (UNKNOWN) [IP] 47462
I got curious and I tried to do the same thing with proxychain just to check which IP would appear, so I run sudo proxychains nmap -O -sV -p 0-65535 IP
The result on the nmap terminal was different I guessed because the limitations of nmap through proxy I read in other places:
But when I checked on the nc terminal the process didn't finish and it doesn't seem that noticed some scan was checking that port. Which is the reason that with proxychains the scan was stealthy?